- Use WinDbg for kernel debugging
- Apply hardware data breakpoint for analyzing data flow
- Understand TDI Network Service
- Understand key I/O data structures such as _IRP and _IO_STACK_LOCATION
- Understand deferred procedure call
- Understand the use of system timer for delayed actions
- Understand the use of WorkItem queue and worker routines
- Operating Systems
- Assembly Language
- Operating System Security
We now finish the last part of raspppoe.sys and look at its malicious actions regarding the use of deferred procedure call (DPC) and establishment of a TCP connection to remote server. We show how to use WinDbg to find out an encrypted configuration file that contains the list of malicious servers (IP and domain names) that Max++ tries to contact. In this tutorial, combined with Tutorial 24, we also show the multi-thread tricks played by Max++ to make the analysis harder. The network activity (setting up TCP connection and sending and processing data) is accomplished via multiple threads. This creates trouble in debugging.
Our analysis starts from _+38A1.
2. Lab Configuration
We will use the instructions of Section 2 of Tutorial 20. In the following we just remind you of several important steps in the configuration:
(1) You need a separate image named "Win_Notes" to record and comment the code. You don't really need to run the malware on this instance, but just to record all your observations using the .udd file. To do this, you have to modify the control flow of IMM so that it does not crash on .sys files. See Section 2 of Tutorial 20 for details. Jump to 0x100038A1 to start the analysis.
(2) The second "Win_DEBUG" image has to be run in the DEBUG mode and there should be a WinDbg hooked from the host system using COM part -- so here, we are doing kernel debugging.
(3) Set a breakpoint "bu _+38A1" in WinDbg to intercept the driver entry function.
3. Code Starting at _+38A1
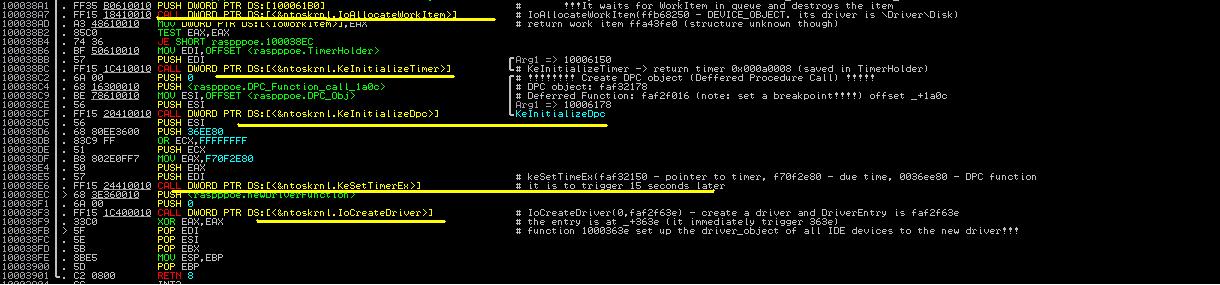 |
| Figure 1. Last Part of rasppoe.sys |
As shown in Figure 1 (first highlighted part), the first call is IoAllocateWorkItem(PDevice_Object). It produces a structure named IO_WorkItem that describes a work item for system threads. Using WinDbg, we can easily identify the device_object passed to the call.
kd> dt _DEVICE_OBJECT ffa50bb8 -r1
nt!_DEVICE_OBJECT
...
+0x010 DriverSize : 0x8e00
+0x014 DriverSection : 0x8131d310 Void
+0x018 DriverExtension : 0x81131888 _DRIVER_EXTENSION
+0x01c DriverName : _UNICODE_STRING "\Driver\Disk"
Then the created IoWorkItem is saved to a global variable.
Challenge 1. Find out when the IoWorkItem is used using data breakpoints.
The next step performed is a call to KeInitializeTimer and the timer object is also saved in a global variable.
Challenge 2. Find when and how the timer is used.
As shown in Figure 1, the subsequent action is a call to KeInitializeDPC. This is an important call. According to MSDN document [1], the prototype of KeInitializeDPC is shown below. Here DPC means deferred procedure call. It is frequently used to service I/O requests (so that low priority calls will be executed later). The function creates and stores a _DPC structure in its first parameter, and registers a function as a second parameter.
VOID KeInitializeDpc( __out PRKDPC Dpc, __in PKDEFERRED_ROUTINE DeferredRoutine, __in_opt PVOID DeferredContext );
Using WinDbg, we can soon infer that the deferred procedure to call later is located at _+3016.
kd> p
_+0x38c2:
faf4f8c2 6a00 push 0
kd> p
_+0x38c4:
faf4f8c4 6816f0f4fa push offset _+0x3016 (faf4f016)
kd> p
_+0x38c9:
faf4f8c9 be7821f5fa mov esi,offset _+0x6178 (faf52178)
kd> p
_+0x38ce:
faf4f8ce 56 push esi
kd> p
_+0x38cf:
faf4f8cf ff152001f5fa call dword ptr [_+0x4120 (faf50120)]
We can set a breakpoint at _+3016 (bp _+3016) and see what is going on.Next, Max++ calls another interesting function KeSetTimerEx to link all the previous actions together. According to [2], the prototype of KeSetTimerEx is listed in the following:
BOOLEAN KeSetTimerEx(
__inout PKTIMER Timer,
__in LARGE_INTEGER DueTime,
__in LONG Period,
__in_opt PKDPC Dpc
); The KeSetTimerEx uses a previously constructed timer to set an "alarm" so that after some
timethe DPC procedure that _+3016 is triggered.
Challenge 3. Prove that the alarm will trigger _+3016 15 seconds later.
4. IO Worker Routine that Connects to Server
Figure 2 shows the function body of _+3016. It's mainly a call to IoQueueWorkItem.
 |
| Figure 2. Function body of _+3016 |
VOID IoQueueWorkItem(
__in PIO_WORKITEM IoWorkItem,
__in PIO_WORKITEM_ROUTINE WorkerRoutine,
__in WORK_QUEUE_TYPE QueueType,
__in_opt PVOID Context
);
Using WinDBG to dump the stack contents, we can easily infer that the WorkerRoutine is located at _+1a0c (in our fiture: it's named DPCWorkItemFunc_connects_to_server). We now proceed to the analysis of _1a0c. By MSDN [4], WorkerRoutine should have the following prototype:
VOID WorkItem(
__in PDEVICE_OBJECT DeviceObject,
__in_opt PVOID Context
)
We now proceed to analyze the worker routine _+1a0c. At the first instruction of _+1a0c, we dump the stack contents as following:
kd> dd esp
fafb3d64 80564610 8114edf0 00000000 805622fc
fafb3d74 fafb3dac 804e426b 81227cb0 00000000
fafb3d84 812e9da8 00000000 00000000 00000000
fafb3d94 00000001 80562334 00000000 812e9da8
fafb3da4 00000000 805645fd fafb3ddc 8057aeff
fafb3db4 81227cb0 00000000 00000000 00000000
fafb3dc4 fafb3db8 00000000 ffffffff 804e2490
fafb3dd4 804f8ab0 00000000 00000000 804f88ea
kd> dt _DEVICE_OBJECT 8114edf0 -r1
nt!_DEVICE_OBJECT
...
+0x01c DriverName : _UNICODE_STRING "\Driver\Disk"
...
Clearly, here 80564610 is the return address, 8114edf0 is a device object (see the prototype of WorkItem routine above), and 0x0000 is the context. You can verify that 8114edf0 is a disk device. Figure 3 shows the simple function body of _+1a0c. It consists of only 4 instructions. At 10001A0E, it pushes the offset of an object attributes into the stack and then it calls a function (readConfig_ConnectToServer) located at _+18d6.
 |
| Figure 3. Worker Item Routine |
kd> dt _OBJECT_ATTRIBUTES faf4a050
nt!_OBJECT_ATTRIBUTES
+0x000 Length : 0x18
+0x004 RootDirectory : (null)
+0x008 ObjectName : 0xfaf482e8 _UNICODE_STRING "\??\C2CAD972#4079#4fd3#A68D#AD34CC121074\{49B474EB-92D0-464f-B1DD-1F37AABF9D95}"
+0x00c Attributes : 0x40
+0x010 SecurityDescriptor : (null)
+0x014 SecurityQualityOfService : (null)
5. Read Configuration File in Hidden Drive and Connect to Remote Server
 |
| Figure 5. First Part of _+18d6 |
kd> db fafb3b3c
fafb3b3c 3c 69 70 3e 38 35 2e 31-37 2e 32 33 39 2e 32 31 <ip>85.17.239.21
fafb3b4c 32 3c 2f 69 70 3e 3c 68-6f 73 74 3e 69 6e 74 65 2</ip><host>inte
fafb3b5c 6e 73 65 64 69 76 65 2e-63 6f 6d 3c 2f 68 6f 73 nsedive.com</hos
fafb3b6c 74 3e 4e 80 98 3b fb fa-12 cc 51 80 08 00 00 00 t>N..;....Q.....
fafb3b7c 00 00 00 00 98 3b fb fa-2e cc 51 80 01 20 f1 df .....;....Q.. ..
fafb3b8c 02 02 00 00 5d 34 4e 80-4a 61 00 00 f6 32 4e 80 ....]4N.Ja...2N.
fafb3b9c fd 32 4e 80 12 c6 05 fb-30 00 00 00 38 3c fb fa .2N.....0...8<..
fafb3bac 08 56 6f 80 00 0d db ba-08 40 00 00 00 00 00 00 .Vo......@......
Challenge 1: replicate the success to find out the contents of the configuration file of Max++.
Figure 6 shows the rest of function _+18d6. The logic is very clear. At 0x10001983, it calls a self-defined function getTagContent (located at _+1486) to look for a tag <ip> in the configuration file. It soon finds out the ip string 85.17.239.212. Then it calls system function RtlIpv4StringToAddressExA to generate the 32-bit representation of the IP address.
Challenge 2. Analyze function _+1486 (getTagContent). What are its parameters and output?
 |
| Figure 6. Rest of Function _+18d6 |
kd> dd esp
fafb3a28 d4ef1155 00005000 00000001 ffb4b850
fafb3a38 812e9da8 652e7ecd a4362152 3c135905
fafb3a48 ee8d12d7 d1b04962 0150df55 0fd8ad5f
It is not hard to see that d4ef1155 is the integer representation of IP address 85.17.239.212 (note the byte sequence and the HEX translation, e.g., 0x55 is decimal number 85).
6. Establish the TCP Connection
Function _+1832 establishes a TCP connection to the 85.17.239.212/5000, however, it does not send anything. The TDI_SEND operation is actually issued by the system thread discussed in Tutorial 24. Why doesn't Max++ try to accomplish in one thread? It's creating trouble for analysts.
Figure 7 presents the function body of _+1832 here. We omit most of the analysis and leave the details to you.
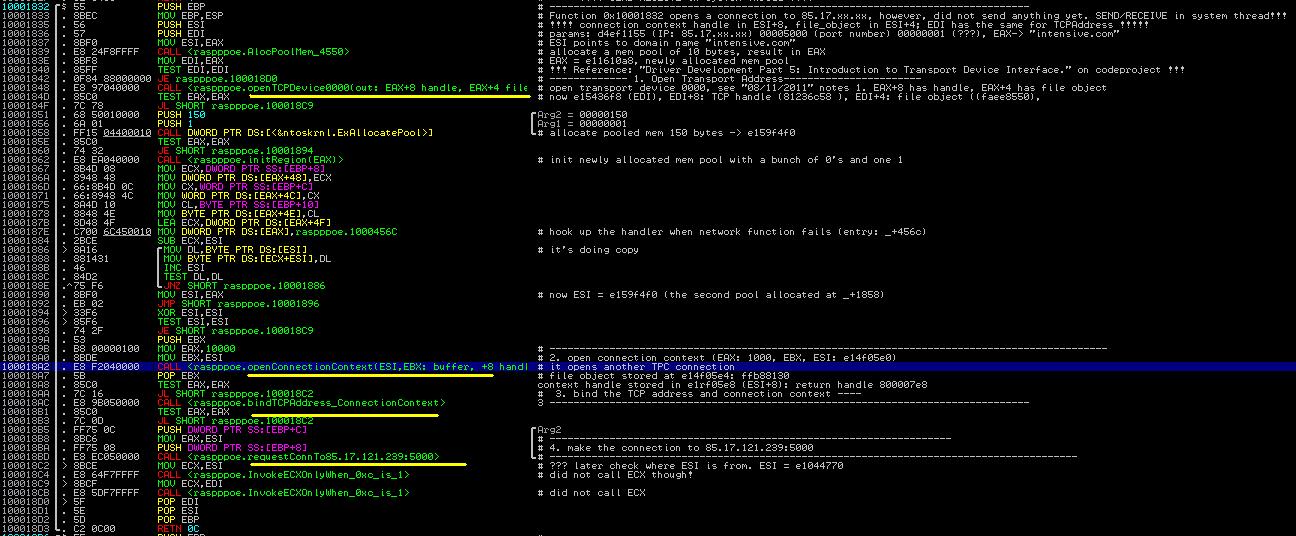 |
| Figure 7. Establish the TCP Connection |
As shown in Figure 7, Max++ follows the general procedure of establishing a TCP connection -- it first binds the address and then requests the connection.
Challenge 4. Completely analyze all the details of function _+1832
References
1. MSDN, "KeInitializeDPC routine", available at http://msdn.microsoft.com/en-us/library/windows/hardware/ff552130(v=vs.85).aspx.
2. MSDN, "KeSetTimerEx routine", available at http://msdn.microsoft.com/en-us/library/windows/hardware/ff553292(v=vs.85).aspx
3. MSDN, "IoQueueWorkItem", available at http://msdn.microsoft.com/en-us/library/windows/hardware/ff549466%28v=vs.85%29.aspx
4. MSDN, "Work Item Routine", available at http://msdn.microsoft.com/en-us/library/windows/hardware/ff566380%28v=vs.85%29.aspx
ReplyDeleteThanks for sharing, very informative blog.
ReverseEngineering
Nice blog!!!!!!!.
ReplyDeleteReverseEngineering
This website offers the best gaming conditions for new players as well as advanced players. Open such gambling platform to start making money online.
ReplyDeleteI don’t even know how I ended up here, but I
ReplyDeletethought this post was great. I don’t know who you are but certainly youare going to a famous blogger if you aren’t already😉 Cheers!
Here is the link of another 2021 Free editor Carck:
https://softserialskey.com/magix-photostory-deluxe-crack/
Beautiful moments get better when you share them with others.
Use PhotoStyle Deluxe to turn important Christmas photos, family celebrations, and everyday little surprises into animated presentations.
Repeat your best moments with your friends and family.
instructions to reset & Fix HP Laserjet Pro M1132 Error Code E8 is being shown hp laserjet m1132 mfp errer E3. Question about LaserJet M4345 MultiFunction Printer.
ReplyDeletethis is is an extremely unique piece of conten writing, along with a great topic to be chosen. If you want math assistance with writing blogs due to lack of time, you can head to
ReplyDeletemath assignment solver The services are offered by expert writers offering Assignment help.You
Great Article
ReplyDeleteCyber Security Projects
Networking Security Projects
JavaScript Training in Chennai
JavaScript Training in Chennai
The Angular Training covers a wide range of topics including Components, Angular Directives, Angular Services, Pipes, security fundamentals, Routing, and Angular programmability. The new Angular TRaining will lay the foundation you need to specialise in Single Page Application developer. Angular Training
Searching for CIPD modules assignment writing ? yes then UAE Assignment Help offers best CIPD assignment writing from UAE experts team. we provide great services at very low cost and delivered quality content on time.
ReplyDeleteFacing trouble to open Quicken? Here are the quick steps to eliminate the problem along with you will also learn how to quicken won’t open issue.
ReplyDeleteThanks for sharing this informative blog, keep sharing informative content blog.
ReplyDeleteTraditional media such as television and radio do not play well in
small and medium enterprises in India. It means that they work magnificently for large corporations. This leads to the need for low-cost social media and digital marketing for SMEs.
Seeking the technical aid to instantly solve QuickBooks Error 15241? Aren’t you able to resolve this particular error due to a lack of technical knowledge? If really it is so, then don’t feel blue! We are on-call tech support specialists providing world-class solutions in an optimum way to all needy customers. You can contact us simply via a toll-free number and discuss your QuickBooks issues frequently. We will deliver you the top-quality fixing guide at your doorstep. By continuously following the provided instructions you can sort out such an error code in very less time. We are professional tech-savvy and present all day all night for your better support and assistance. Thus, feel free to consult us!
ReplyDeleteThe fax error 388, when you try to send a fax, the fax machine originates the fax session and also spots the fax device to which you are trying to send the fax but can’t identify the T30 framework. If you see your fax machine in V.17 mode then the issue must be with a link.
ReplyDeleteThanks for sharing post, taking the online business to the next level might appear a big challenge but you can do it by exploring the cheapest Smm panel The online website of business works when people visit the website and place the orders after their satisfaction with the product available over there.
ReplyDeleteThanks for sharing post, Not to mention the most modern party centers in the city, both locals and travelers come here to have a lot of fun. For the energetic crowd, these lively nightlife Delhi tourist places destinations in Delhi are some of the important tourist places in Delhi. India Gate, Red Fort, Qutub Minar, Khauz Khas, Bahai Temple (Lotus), Chandni Chowk, Jama Masjid, Sarojini Nagar Square.
ReplyDeleteHi, I am Jonsen Drill, I am working as a tech expert at email support. I have 3 years of experience in this field. If you have any problems related to Roadrunner email settings problems, etc, then please contact me for instant help related to email problems
ReplyDeleteinkjet mosaic manufacturer
ReplyDeletewaterjet mosaic manufacturers
In this post, we will show you how to Move Quicken To A New Computer. Stay here to learn the best possible directives of transferring Quicken from one PC to another.
ReplyDeleteAre you struglging with how can we use quickbooks point of sale then here is the complete guide through which you can use this point of sale on your own with no efforts.quickbooks point of sale online training
ReplyDelete
ReplyDeleteGet answers to all your questions related to Cash App Dispute Payment:
Cash App Dispute Payment is one of the major issues that people frequently face on the cash app. If you are a victim of this problem then contact the support team to get answers to your queries. Cash app representatives will tell you the scenarios where you can raise a dispute to get your only back from the merchant.
Security is the main part of computer. We use different softwares for protect the computer from viruses. You deliver informative information about Deferred Procedure Call (DPC) and TCP Connection, This post is very informative and useful for IT persons. Furthermore Due to water lacking and garbage, gutter walls can be gamage, for this purpose. Gutter Cleaning Services In Oakland Ca provide the best service at affordable price.
ReplyDeleteFound your post interesting to read. I cant wait to see your post soon. Good Luck for the upcoming update.This article is really very interesting and effective.
ReplyDeleteThanks for sharing this knowledgeable information with us, truly a great informative site.Myassignmenthelp gives scholastic myassignmenthelp to understudies with the goal that they can feel unwind and center around another significant thing in their life. We have numerous expert experience content essayists to give you the best to your work.
ReplyDeleteThe way you explain amabassador and contributor is fantabulous. This is so informative. I am sure every one will love this blog.
ReplyDeleteIf you are looking for online grocery shopping in Durgapur, download Bazaar Durgapur app from Playstore. Your one stop grocery solution. Opt for combo offer for bigger discounts.
ReplyDeleteCheers mate. I will make writing better! Your research work can be a paper helper or a number of engineering topics for the project. However, choosing an influencer is still a challenge. Hence, students often need to list some compelling topics to write their technical papers. Meanwhile, it should also be remembered that the selected topic will contain enough information to meet the word limit.
ReplyDeleteAre you looking for the best online assignment help in the United Arab Emirates? Look no further as we provide reliable assignment writing to the students so they contact us for writing assistance. It provides the best support system to the students so that they can contact anytime and get expert assistance.
ReplyDeleteSuperapid is one of the leading cnc lathe machining services. We offer milling services and have the best capabilities in current technology and manufacturing that can achieve good results with precision machining.
ReplyDeleteIf you have any doubt on how to get services forassignment help in Australia in your academic paper, then reach out to us and get help from our experts.
ReplyDeleteThis is a smart blog. I mean it. You have so much knowledge about this issue, and so much passion. You also know how to make people rally behind it, obviously from the responses.
ReplyDelete토토사이트
온라인카지노
파워볼사이트
카지노사이트
Right away this website will probably unquestionably usually become well known with regards to most of website customers, as a result of meticulous accounts and in addition tests.
ReplyDelete스포츠토토
토토
안전놀이터
토토사이트
Wonderful article, thank you for sharing the info. It isn’t too often that you simply read articles where the poster understands what they’re blogging about.
ReplyDelete사설토토
카지노
파워볼사이트
바카라사이트
Very Informative & watchful content, You guys also try it
ReplyDeleteReal Estate Agencies Meridian ID
for best Relocation services
Really good post. I am looking to contact you further. Do assignment writing causes sleepless nights? Sourceessay.com is the best platform to explore maximum number of write that essay services from experts.
ReplyDeleteA few students decide to study in the Australia inferable from the explanation that this nation is home to esteemed colleges and colleges, which consistently stay in the fantasy rundown of researchers. With fantastic scholastic offices and instruction principles, numerous urban communities in the Australia invite global students. These college-attendees work day in and out to dominate in scholastics, yet with regards to composing pascal assignments, they face many difficulties. From time requirements, trouble in coding, language issues to inaccessibility of bona fide research sources, they face many worries. All of this moves them to look for pascal assignment help Australia services. myassignmenthelp
ReplyDeleteNice blog.A manual lathe machine
ReplyDeleteis a machine tool that spins the workpiece around an axis while cutting against the cutting tool's edge. The resulting workpiece is symmetrical around the rotation axis.
You can tell when your projects make a difference from the crowd. There's something unique about the projects. It appears to me that they are all amazing! the smm panel in india
ReplyDeleteYou can tell when your projects make a difference from the crowd. There's something unique about the projects. It appears to me that they are all amazing! the best smm panel india
ReplyDeletePaypal is one of the leading payment transfer apps in the recent era. Most of us are well aware of PayPal and how it works. In this blog, I am going to answer some of your frequently asked questions and also teach you how you can create an account in PayPal. Paypal has a strong customer base with 286 million active customers and it is increasing day by day. The reason behind this success of PayPal is there exciting features like one-tap pay gives customer relief. The most important thing about PayPal is that you have to worry about your banking credentials.
ReplyDeletePayPal Login |
primevideo.com/mytv |
amazon.com/code |
hbomax.com/tvsignin |
www.amazon.com/mytv |
You can tell when your projects make a difference from the crowd. There's something unique about the projects. It appears to me that they are all amazing! the trusted smm panel
ReplyDeleteNice article Conflict Management Assignment Help Chicago
ReplyDeletewebgirls When it comes to preventing infections, patients often times have their operate remove on their behalf. This is because infections can certainly come to be constant and continuous. Bearing that in mind, on this page, we are going to current a variety of the best proven candida albicans therapy and reduction tips around.
ReplyDeletehttps://gamebegin.xyz You can training by itself. A pitching device permits you to establish the pace in the golf ball. By launching a number of baseballs to the device, you are able to process reaching without needing a pitcher. This electrical unit is perfect for individuals who wish to practice baseball by itself. Pitching equipment could be picked up in your community wearing merchandise store.
ReplyDeletehttps://gameboot.xyz You see them on publications and so on Tv set, men and women who appear to be their hands and thighs will explode as his or her muscles are really massive! There is no will need so that you can acquire your body for that degree if you don't prefer to, as being the simple techniques on this page will help you to construct muscle mass inside a healthier method.
ReplyDeleteFind a service like ours if you need research assistance; we've been in the academic writing business for over five years. Coursework writing is particularly difficult for beginners, but you can obtain online coursework help from writers.
ReplyDeleteI really found you by mistake, while I was browsing on Yahoo for something else,
ReplyDeleteAnyways I am here now and would just like to say kudos for a tremendous post
IDM Crack
Ezdrummer Crack
Windows 10 Activatior Crack
REFX Nexus VST Crack
Virtual Serial Ports Crack
Kerio Control Crack >
Do you have experience with the best validators?
ReplyDeleteLet me introduce myself to you.
토토커뮤니티
QuickBooks is among the popular software used for accounting and bookkeeping. QuickBooks provides you with a feature of direct deposit quickbooks file types to pay to your employees. It will allow you to transfer money to the direct bank accounts immediately or most probably within 2-3 days. In case you are already using the QuickBooks payroll service then you can change the bank account to the other bank account to set up the qb direct deposit form and you check also quickbooks error 6094
ReplyDeleteAs the QuickBooks online enterprise expands, it makes sense that they need to grow their library of QuickBooks file extensionsto accommodate the big data. QuickBooks Desktop uses different file types to express varying forms of information. For example, your main company files (QBW) are in a whole other realm than the backup data files (QBB).
ReplyDeleteIf something went wrong during the QuickBooks install, it could cause a problem when you try to QuickBooks activation not working. Run the QuickBooks Install Diagnostic Tool to fix common install issues.
ReplyDeleteVery nice article and straight to the point. I don’t know if this is truly the best place to ask but do you folks have any idea where to get some professional writers? Thank you. 파친코
ReplyDeleteThis is the right blog for anyone who wants to find out about this topic. You realize so much its almost hard to argue with you (not that I actually would want…HaHa). You definitely put a new spin on a topic thats been written about for years. Great stuff, just great! 슬롯머신사이트
ReplyDeleteWhen you go to pay for something online with your capital one access code we'll sometimes ask you to enter a one-time passcode (or OTP for short), so we know it's really you. It's a unique 6-digit number that we send as a text or automated voice message to the mobile or landline number of your choice.
ReplyDeleteHow to Use QuickBooks Time Tracking | QuickBooks provides an all-in-one time tracking solution and offers easy, accurate time tracking insight. Some of the highlights of QuickBooks' time tracking solution include the abilities to: Track, submit, and approve employee time on the go. Monitor overtime and paid time off (PTO) with alerts || Hii Guys in my blog we provide a complete Guide Of use setup and errors solution have an any issue related of Quickbooks please click the you can get the pro-advisores 24*7 Helpline Numbes
ReplyDeleteWe have talked with one of the Oily skin person Rosy. "My skin was so oily since childhood and it was really irritating for me. I can't be confident even while i go to party or else to a function, everyone stares at my oil skin and i have to feel the shy. This is where I came across the https://yugloskin.com from the Yuglo skin where the https://yugloskin.com/products/face-oil is one of the best products which makes my face very smooth, free from oil and looks so great. Since then I have become an evid fan of the natural skin care brand. Especially the Natural Ingredients makes the brand so unique because these days we are seeing so many chemicals used products. Even though, their results might be faster but in the long run, we are going to have issues while using such kind of brands. Hence I recommend Yuglo for any women who is looking for organic and natural products for their hair, face and skin".
ReplyDeleteWhile when we got the opportunity to speak with one of the dry skin women Ily. Ily said "My skin was dry all the time and it is really frustrating experience for me, especially, I stay in the cold regions and when there is heavy cold, you can clear see the layers coming out from the lips and skin due to dryness, that is where i tried the https://yugloskin.com/products/lip-mask from the Yuglo. I apply it at thee night time before i sleep and while i woke up in the morning, i am going to have a great and nice experience, My skin feels better and i also tried the https://yugloskin.com/products/skincare-face-masks from this organic brand. I applied it for a month and you don't and you don't believe me the results are fantastic. I am using both their Peach Lips mask and Face mask for the skin since past 2 years and i would love to try their new products as well in the future. Thanks to the yuglo skin for bringing such awesome products and great thing is they are available at an affordable pricing. It merely costs me $25 per month to try their products and have a healthy skin routine.
Types of Products to improve Skin Care
When it comes to the types of the products, there are so many people who are trying the natural face masks by seeing the youtube videos and improving their skin care. There are majorly three types of skins, one is oily, the other is dry and the third one is mixed. Especially those with Oily skin always suffer due to their face looks quiet odd due to the excess oil on their face and they feel so bad about it.
This is where the Organic products of skin care has come in handy for these kind of people. While people who are having a mixed dry and oily skin, not had to suffer much but still they can improve their skin tone using the Lip mask product from amazon. This product is bought by more than 100000+ happy customers and has an average rating of 4.5 with more than 5500 reviews.
They have products which are related to hair, face and lips. Especially their lip sleeping mask is the best seller and next comes, the face mask which is also quiet good seller for them. They also have face oil and new vanilla flavor for the lips, they want to become one of the top skin care brands in the future by solving all the issues related to the skin care. They also have the face moisturizer which is one of the best among the face moisturizers compared to others as those comes with the natural ingredients which everyone will love than compared to unnatural and chemical ingredients.
Are you looking to buy Best Wooden Sofa Design In India with all products which are designed by the best Wooden India Most wooden sofas were traditionally made of wood, but wooden sofas have been made of cork, and bamboo, or other materials? It is made from the best quality wood and designed with the utmost attention to detail. Follow the link here and get to know which is the Best Wooden Sofa Design In India Best Wooden Sofa Design In India
ReplyDeleteThe Best cycle under 20000 is among the most popular categories in cycle touring. This range of prices is designed to appeal to the large majority of cycle tourers who are not interested in the most extreme and expensive machines. The key here is comfort and range. You still need the strength and efficiency to make long tours, but you don't need to sacrifice to get there. Hit the link here and get to know Cheapest Best Cycle Under 20000 In India Best Wooden Sofa Design In India
ReplyDeleteMany students try but fail to complete their tasks on time and with decent grades. For those who are short on time, we provide the best assignment help in Australia. Our internationally acknowledged academic professionals provide the best online assignment help services to students who are dealing with assignments and want to finish them as soon as feasible.
ReplyDeleteThe QuickBooks unrecoverable error code is indicated when you open the company file or while clicking on save, print, or ship icon. These minor errors do not indicate that anything incorrect has been saved on the computer. It can be solved by closing the software application and opening it again. The QuickBooks unrecoverable error shows up when you are using the accounting software. These error codes prompt users with a recording by itself or throw some other critical errors. The numbers in QuickBooks unrecoverable error indicate where the error lies in the program. The QuickBooks unrecoverable error is nothing to worry about. All you need to do is to go through the step by step instructions and resolve them. This can be done by taking help from the QuickBooks technical support. For additional information, visit us at www.quickbooks-intuit.ca. QuickBooks accounting software is one of the most popular platforms by Intuit.QB unrecoverable error is also prone to errors and difficulties, due to which the company has introduced error codes. If you get any of these errors while working on your accounting software, make sure to check the following steps to fix them.
ReplyDeleteSage Fixed Assets Support Number gives you the flexibility to manage and optimize your fixed assets throughout their useful life. Learn how our powerful depreciation calculation engine and intuitive reporting simplify asset management and accounting across your business.
ReplyDeleteSage provides a Sage Payroll Support Number service for all Sage payroll systems, with over 350 technical advisors all trained to support Sage software.
You can contact a Timeslips certified consultant or Sage Timeslips Support Number person, who might be able to help you correct the corruption.
Sage Online Support Number One is a family of online accounting and business services for small businesses. Choose your country to get started.
trending technology
ReplyDeleteblogging platforms
advantages of blogging platforms
Guest Post
trending technology
Awesome Blog with good stuff
ReplyDeleteFreelance Marketplace
Very Interesting Post, thanks for sharing. plex tv link
ReplyDeleteThis is very useful software for you and me. No errors were found during the check.
ReplyDeleteYou can use it. I hope you like it. plex tv code
I'm impressed, I must say. Actually rarely can i encounter a blog that's both educative and entertaining, and without a doubt, you could have hit the nail about the head. Your idea is outstanding; the thing is something that too few individuals are speaking intelligently about. We are delighted that we came across this around my try to find some thing with this.메이저사이트
ReplyDeleteThe game has been played since time immemorial and has been popular in many parts of India, especially in Maharashtra.fixmatkais a gambling game that is popular in India. It is a game of chance and involves predicting the numbers or patterns that would appear on the matka
ReplyDeletevery nice content
ReplyDeleteBuy sex toy in india on Adultslove
Thank you so much admin for uploading such amazing content with us your blog is really helpful for me.
ReplyDeleteIt was very informative to read, thanks! I would like to welcome you to our educational website where we provide such services as writing georgetown university supplemental essays online in a very short time. Our customers are very satisfied with the works given.
ReplyDeleteHello, Thank you for your meaningful words which is easily understand by people,it would really helpful for the proper workflow. Thankyou for sharing this wonderful article , 초콜릿
ReplyDelete초콜릿
초콜릿
초콜릿
초콜릿
초콜릿
초콜릿 We are also sharing the blogs on the topic of Gaming software which is helpful for playing games on pc if you want to read it then kindly visit here
I read your post well. It's full of very interesting stories.It's great how you can think of that.
ReplyDeleteThank you for giving this insightful information.
ReplyDeleteJava programming is one of the most important subjects to understand. Students realize the need of comprehending the subject by putting in dedication. To excel with grades, students may need professional Java Programming Assignment Help and we provide that. Get instant assistance today!
Get The Best Big Data Analytics Assignment Help
ReplyDeleteContact us or send us your big data project if you need assistance with ASG services. If you need Big Data homework assistance, go no further than us on the web. Our top big data analytics assignment help
specialists serve clients worldwide, including the United States, Great Britain, Australia, Germany, the United Arab Emirates, New Zealand, and others.
Manochikitsa is an organization that has the goal of bettering people & their lives and works hard toward that end by providing the Best Online Counselling in India Everyone has a desire for someone who will just listen to them. An someone who is able to listen without passing judgement, comprehend, and maybe even contribute to the process of finding a solution.
ReplyDeletebike pump
ReplyDeleteslot siteleri
ReplyDeletekralbet
betpark
tipobet
betmatik
kibris bahis siteleri
poker siteleri
bonus veren siteler
mobil ödeme bahis
YJQHYP
Hi thank you for share valueable information are you looking for best assignment in australia
ReplyDeleteJava Programming Assignment Help is the perfect solution for students who need help with Java homework, course work, or projects. best online java programming assignment help ! Our experienced and qualified tutors are available 24/7 to help with your questions and problems.
ReplyDeletebahis siteleri
ReplyDeletehttps://bahissiteleri.io
youwin
bets10
1xbet
MWEWS
ReplyDeleteIt’s amazing, very talented and highly skilled blogger, very satisfied with your excellent post, looking forward to more of your useful thought, thanks for sharing. plapoly(nsuk-affiliated) postgraduate admission form
wow! thank you for sharing this blog.Looking for R Studio assignment help? Our experts provide top-notch assistance with R Studio assignments, ensuring you get the grades R Studio Assignment Helpyou deserve. Get in touch today to learn more!
ReplyDeleteIn the realm of classic short stories, O. Henry's "The Last Leaf" stands as a testament to the enduring power of hope, sacrifice, and friendship. This timeless tale, set against the backdrop of a harsh winter in Greenwich Village, weaves a narrative that captivates hearts and minds. Join us as we delve into the essence of "the last leaf summary" in this comprehensive summary.
ReplyDeleteGain valuable insights into marketing assignment report with our comprehensive marketing assignment report.
ReplyDelete십시오. 토토사이트 제작
ReplyDeleteCool stuff 스타스포츠토토
ReplyDeleteThis is a 에이전트토토
ReplyDelete[url=https://www.procurementresource.com/resource-center/sulfuric-acid-price-trends]Sulfuric acid prices[/url]
ReplyDelete, influenced by various factors including supply, demand, and production costs, have experienced fluctuations in recent years. As a key nitrogen-based fertilizer, urea plays a crucial role in global agriculture, impacting crop yields and food production. Shifts in energy prices, natural gas availability (a primary component in urea production), geopolitical tensions, and weather patterns can all contribute to the volatility of urea prices. This volatility often affects agricultural input costs, impacting farmers and the overall food supply chain. Monitoring and understanding these price movements remain essential for both agricultural stakeholders and consumers worldwide.
You are a student and need help with marketing assignment, here We are the global assignment expert. We offer assignment services to the students and delivers plagiarism free assignment. Global assignment help has a team of knowledgeable and experienced scholastic writer with 5 plus year of experience. Our team will help you with your assignment and they will also try to clear your doubt related with your assignment. So stop your search here, and connect with us on our website and give us chance to serve you better.
ReplyDeleteVery good article, thanks for sharing.
ReplyDeletematka
Great article! If you're tackling complex data analysis projects and need some assistance, consider R Studio Assignment Help. It's a fantastic resource for mastering R programming, data visualization, and statistical analysis. Don't struggle alone—get the expert guidance you need to excel in your assignments and enhance your data-driven decision-making skills.
ReplyDeleteGet top-notch Law assignment help from qualified experts. We offer personalized support to enhance your understanding and improve your grades in legal coursework.
ReplyDeleteIf you're looking for assistance with your assignments, you’ve come to the right place! Our blog offers valuable insights and resources tailored to help you succeed in your studies. For those struggling with complex topics, especially in taxation, don’t hesitate to seek Taxation Assignment Help. Our expert advice and guidance will enhance your understanding and boost your academic performance!
ReplyDeleteThis post is really astounding blog to read! Keep it up man
ReplyDeleteI was delighted to read this kind of article, very much useful. Many thanks
ReplyDeleteAwesome! Be benefit some information provided here. Thanks a lot for this
ReplyDeleteWow, awesome blog layout! This web site is so great, Cheers!
ReplyDeleteVery informative article.
ReplyDeletesara777
Thank you very much for sharing this great post
ReplyDeletesara 777 app download
Achieve academic success with our Mechanical Assignment Help. We provide comprehensive support and expert insights to tackle your toughest challenges.
ReplyDeleteAchieve academic success in Electrical Engineering Assignment Help
ReplyDeletewith our dedicated assignment help. Expert guidance is just a click away to enhance your learning experience.
Thank you for sharing informative article.
ReplyDeletegama567
Thank you for sharing this excellent knowledge with us.
ReplyDeletesara 777
غسيل مكيفات بالاحساء 4vdRQa1c3I
ReplyDeleteيمكن القول إن شركة عجمان لفحص شبكات المياه تُعَدُّ ضرورية لأي مجتمع يسعى للحفاظ على منشآته آمنة وصحية، إن خدمات الشركة تسهم في كشف المشكلات بشكل مبكر، مما يُساعد في تقليل التكاليف المرتبطة بالإصلاحات التي قد تُصبح مُكلفة إذا ما تُركت للمصادفة، من خلال التعاقد مع شركة عجمان، يضمن العملاء الحصول على استشارات موثوقة وحلول فعّالة لمشاكل الرطوبة وعيوب الشبكات المائية، مما ينعكس إيجابًا على جودة الحياة بشكل عام .
ReplyDeleteكشف تسربات المياة في عجمان
Very nice blog, Thanks for sharing great article.
ReplyDeleteAlso read
Economics is a subject that requires strong analytical thinking, critical reasoning, and a good grasp of mathematical concepts. However, due to its complexity, many students find it challenging to complete assignments accurately and on time. Economics Assignment Help provides expert guidance, accurate solutions, and customized support, enabling students to excel academically while reducing stress. With professional assistance, learners not only achieve better grades but also develop the skills and confidence necessary to succeed in the dynamic field of economics.
ReplyDeleteكل الشكر والتقدير اعمال مميزة ايضاء تستحق شركة "ولاد البلد" التحية والتقدير على الخدمة المتميزة التي تقدمها في مجال الخدمات المنزلية. يُعزز الالتزام بالجودة والاحترافية من سمعتها كمزود أساسي للخدمات التي تناسب متطلبات الحياة الحديثة. مستقبل الشركة يبدو واعدًا، حيث تستمر في تطوير خدماتها وتوسيع شبكة عملائها، مما يجعلها الخيار الأول لعائلات كثيرة تبحث عن الراحة والموثوقية في خدمات المنزل.
ReplyDeleteولاد البلد خدمة المنزل
ولاد البلد الامارات
ولاد البلد قطر
ولاد البلد مصر
ولاد البلد البحرين
Thank you for sharing this. Statistics Assignment Help provides expert guidance to students in understanding complex statistical concepts, data analysis, and interpretation. It covers topics like probability, regression, hypothesis testing, and ANOVA. Professional tutors assist with assignments, projects, and reports, ensuring accuracy, clarity, and improved grades through step-by-step solutions and reliable academic support.
ReplyDeleteThis is a very insightful tutorial, especially the way you explained Deferred Procedure Calls and their role in maintaining system performance while handling TCP connections. The step-by-step breakdown makes a complex malware analysis concept much easier to understand, even for readers who are still building their foundation in system internals. I also appreciate how you connected low-level OS behavior with real-world malware techniques. Resources like this are extremely helpful for students working on technical coursework, and I can see how guides like this would complement pascal assignment help for learners dealing with system-level programming and security-focused assignments. Great work—looking forward to the next tutorial in the series.
ReplyDelete