- Understand the portable executable (PE) header of binary executables.
- Understand the EXPORT TABLE.
- Practice disassemble and reverse engineering techniques.
- Operating Systems.
- Computer Security.
1. Introduction
In this tutorial, we will analyze the first harmful operation performed by Max++. It changes the structure of the export table of ntdll.dll. Recall the analysis of Max++ in Tutorial 7, the malware reads the information in TIB and PEB, and examines the loaded modules one by one, until it encounters "ntdll.dll" (this is accomplished using a checksum function inside a two layer nested loop).
In this tutorial, we will reverse engineer the code starting at 0x40105C.
2. Background Information of PE Header
Any binary executable file (no matter on Unix or Windows) has to include a header to describe its structure: e.g., the base address of its code section, data section, and the list of functions that can be exported from the executable, etc. When the file is executed by the operating system, the OS simply reads this header information first, and then loads the binary data from the file to populate the contents of the code/data segments of the address space for the corresponding process. When the file is dynamically linked (i.e., the system calls it relies on are not statically linked in the executable), the OS has to rely on its import table to determine where to find the entry addresses of these system functions.
Most binary executable files on Windows follows the following structure: DOS Header (64 bytes), PE Header, sections (code and data). For a complete survey and introduction of the executable file format, we recommend Goppit's "Portable Executable File Format - A Reverse Engineering View" [1].
DOS Header starts with magic number 4D 5A 50 00, and the last 4 bytes is the location of PE header in the binary executable file. Other fields are not that interesting. The PE header contains significantly more information and more interesting. In Figure 1, please find the structure of PE Header. We only list the information that are interesting to us in this tutorial. For a complete walk-through, please refer to Goppit's work [1].
 |
| Figure 1. Structure of PE Header |
As shown in Figure 1, PE header consists of three parts: (1) a 4-byte magic code, (2) a 20-byte file header and its data type is IMAGE_FILE_HEADER, and (3) a 224-byte optional header (type: IMAGE_OPTIONAL_HEADER32). The optional header itself has two parts: the first 96 bytes contain information such as major operating systems, entry point, etc. The second part is a data directory of 128 bytes. It consists of 16 entries, and each entry has 8 bytes (address, size).
We are interested in the first two entries: one has the pointer to the beginning of the export table, and the other points to the import table.
2.1 Debugging Tool Support (Small Lab Experiments)
Modern binary debuggers have provided sufficient support for examining PE headers. We discuss the use of WinDbg and Immunity Debugger.
(1) WinDbg. Assume that we know that the PE structure of ntdll.dll is located at memory address 0x7C9000E0. We can display the second part: file header using the following.
dt nt!_IMAGE_FILE_HEADER 0x7c9000e4
+0x000 Machine : 0x14c
+0x002 NumberOfSections : 4
+0x004 TimeDateStamp : 0x4802a12c
+0x008 PointerToSymbolTable : 0
+0x00c NumberOfSymbols : 0
+0x010 SizeOfOptionalHeader : 0xe0
+0x012 Characteristics : 0x210e
Then we can calculate the starting address of the optional header: 0x7C9000E4 + 0x14 (20 bytes) = 0x7C9000F8. The attributes of optional header is displayed as below. For example, the major linker version is 7 and the the address of entry point is 0x12c28 (relative of the base address 0x7c900000).
kd> dt _IMAGE_OPTIONAL_HEADER 0x7c9000F8
nt!_IMAGE_OPTIONAL_HEADER
+0x000 Magic : 0x10b
+0x002 MajorLinkerVersion : 0x7 ''
+0x003 MinorLinkerVersion : 0xa ''
+0x004 SizeOfCode : 0x7a000
+0x008 SizeOfInitializedData : 0x33a00
+0x00c SizeOfUninitializedData : 0
+0x010 AddressOfEntryPoint : 0x12c28
+0x014 BaseOfCode : 0x1000
+0x018 BaseOfData : 0x76000
+0x01c ImageBase : 0x7c900000
+0x020 SectionAlignment : 0x1000
+0x024 FileAlignment : 0x200
+0x028 MajorOperatingSystemVersion : 5
+0x02a MinorOperatingSystemVersion : 1
+0x02c MajorImageVersion : 5
+0x02e MinorImageVersion : 1
+0x030 MajorSubsystemVersion : 4
+0x032 MinorSubsystemVersion : 0xa
+0x034 Win32VersionValue : 0
+0x038 SizeOfImage : 0xaf000
+0x03c SizeOfHeaders : 0x400
+0x040 CheckSum : 0xb62bc
+0x044 Subsystem : 3
+0x046 DllCharacteristics : 0
+0x048 SizeOfStackReserve : 0x40000
+0x04c SizeOfStackCommit : 0x1000
+0x050 SizeOfHeapReserve : 0x100000
+0x054 SizeOfHeapCommit : 0x1000
+0x058 LoaderFlags : 0
+0x05c NumberOfRvaAndSizes : 0x10
+0x060 DataDirectory : [16] _IMAGE_DATA_DIRECTORY
As shown by Goppit [1], OllyDbg can display PE structure nicely. Since the Immunity Debugger is based on OllyDbg, we can achieve the same effect. In IMM View -> Memory, we can easily locate the starting address of each module (e.g., see Figure 2).
 |
| Figure 2. Getting PE Header Address |
3. Export Table
Recall that the first entry of IMAGE_DATA_DIRECTORY of the optional header field contains information about the export table. By Figure 1, you can soon infer that the 4 bytes located at PE + 0x78 (i.e., offset 120 bytes) is the relative address (relative to DLL base address) of the export table, and the next byte (at offset 0x7C) is the size of the export table.
The data type for the export table is IMAGE_EXPORT_DIRECTORY. Unfortunately, the WinDbg symbol set does not include the definition of this data structure, but you can easily find it in winnt.h through a google search (e.g., from [2]). The following is the definition of IMAGE_EXPORT_DIRECTORY from [2].
typedef struct _IMAGE_EXPORT_DIRECTORY {
DWORD Characteristics; //offset 0x0
DWORD TimeDateStamp; //offset 0x4
WORD MajorVersion; //offset 0x8
WORD MinorVersion; //offset 0xa
DWORD Name; //offset 0xc
DWORD Base; //offset 0x10
DWORD NumberOfFunctions; //offset 0x14
DWORD NumberOfNames; //offset 0x18
DWORD AddressOfFunctions; //offset 0x1c
DWORD AddressOfNames; //offset 0x20
DWORD AddressOfNameOrdinals; //offset 0x24
}
Here, we need some manual calculation of addresses for each attribute for our later analysis. In the above definition, WORD is a computer word of 16 bites (2bytes), and DWORD is 4 bytes. We can easily infer that, MajorVersion is located at offset 0x8, and AddressOfFunctions is located at offset 0x1c.
Now assume that IMAGE_EXPORT_DIRECTORY is located at 0x7C903400, the following is the dump from WinDbg (here "dd" is to display memory):
kd> dd 7c903400
7c903400 00000000 48025c72 00000000 00006786
7c903410 00000001 00000523 00000523 00003428
7c903420 000048b4 00005d40 00057efb 00057e63
7c903430 00057dc5 00002ad0 00002b30 00002b40
7c903440 00002b20 0001eb58 0001ebb9 0001e3af
7c903450 0002062d 000206ee 0004fe3a 00012d71
7c903460 000211e7 0001eaff 0004fe2f 0004fdaa
7c903470 0001b08a 0004febb 0004fe6d 0004fde6
We can soon infer that there are 0x523 functions exposed in the export table, and there are 0x523 names exposed. Why? Because the NumberOfFunctions is located at offset 0x14 (thus its address is 0x7c903400+0x14 = 0x7c903414) For another example, look at the attribute "Name" which is located at offset 0xc (i.e., its address: 0x7c90340c), we have number 0x00006787. This is the address relative to the base DLL address (assume it is 0x7c900000). Then we have the name of the module located at 0x7c906786. We can verify using the "db" command in WinDbg (display memory contents as bytes): you can verify that the module name is indeed ntdll.dll.
kd> db 7c906786
7c906786 6e 74 64 6c 6c 2e 64 6c-6c 00 43 73 72 41 6c 6c ntdll.dll.CsrAll
7c906796 6f 63 61 74 65 43 61 70-74 75 72 65 42 75 66 66 ocateCaptureBuff
Read page 26 of [1], you will find that the "AddressOfFunctions", "AddressOfNames", and "AddressOfNameOdinals" are the most important attributes. There are three arrays (shown as below), and each of the above attributes contains one corresponding starting address of an array.
PVOID Functions[523]; //each element is a function pointer
char * Names[523]; //each element is a char * pointer
short int Ordinal[523]; //each element is an 16 bit integer
For example, by manual calculation we know that the Names array starts at 7C9048B4 (given the 0x48B4 located at offset 0x20, for attribute AddressOfNames; and assuming the base address is 0x7C900000). We know that each element of the Names array is 4 bytes. here is the dump of the first 8 elements:
kd> dd 7c9048b4
7c9048b4 00006790 000067a9 000067c3 000067db
7c9048c4 00006807 0000681f 00006831 00006845
We can verify the first name (00006790): It's CsrAllocateCaptureBuffer. Note that a "0" byte is used to terminate a string.
kd> db 7c906790
7c906790 43 73 72 41 6c 6c 6f 63-61 74 65 43 61 70 74 75 CsrAllocateCaptu
7c9067a0 72 65 42 75 66 66 65 72-00 43 73 72 41 6c 6c 6f reBuffer.CsrAllo
We can also verify the second name (000067a9): It's CsrAllocateMessagePointer.
kd> db 7c9067a9
7c9067a9 43 73 72 41 6c 6c 6f 63-61 74 65 4d 65 73 73 61 CsrAllocateMessa
7c9067b9 67 65 50 6f 69 6e 74 65-72 00 43 73 72 43 61 70 gePointer.CsrCap
Now, given a Function name, how do we find its entry address? The following is the formula:
Note that array index starts from 0.
Assume Names[x].equals(FunctionName)
Function address is Functions[Ordinal[x]]
4. Challenge1 of the Day
The first sixteen elements of the Ordinal is shown below:
kd> dd 7c905d40
7c905d40 00080007 000a0009 000c000b 000e000d
7c905d50 0010000f 00120011 00140013 00160015
The first eight elements of the Functions array is shown below:
kd> dd 7c903428
7c903428 00057efb 00057e63 00057dc5 00002ad0
7c903438 00002b30 00002b40 00002b20 0001eb58
What is the entry address of function CsrAllocateCaptureBuffer? The answer is: it's 7C91EB58. Think about why? (Pay special attention to the byte order of integers).
5. Analysis of Code
We now start to analyze the code, starting at 0x40105C. Set a hardware breakpoint at 0x40105C (in code pane, right click -> Go To Expression (0x40105c) and then right click -> breakpoints -> hardware, on execution). Press F9 to run to the point. The first instruction should be PUSH DS:[EAX+8]. If you see a bunch of BYTE DATA instructions, that's caused by the byte scission of the code. Highlight all these BYTE DATA instructions, right click -> Treat as Command during next analysis and we should have the correct disassembly displayed in IMM.
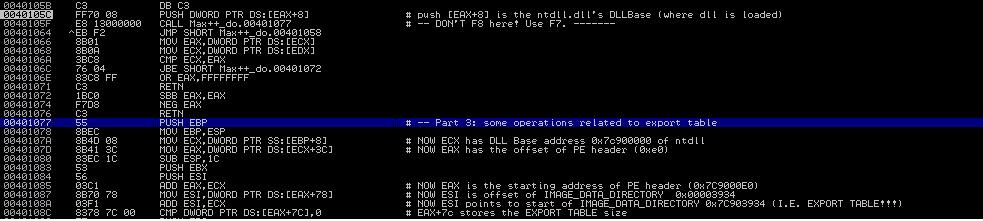 |
| Figure 4: Accessing Export Table |
Now let us analyze the first couple of instructions starting at 0x40105C (in Figure 4). Continuing the analysis of Tutorial 7, we know that after reading the module information (one by one), the code jumps out of the loop when it encounters the ntdll.dll. At this moment, EAX contains the address of offset 0x18 of LDR_DATA_TABLE_ENTRY. In another word, EAX points to the attribute "DllBase". Thus, the instruction at 0x40105C, i.e., PUSH DWORD DS:[EAX+8] is to push the DllBase into the stack. Executing this command, you will find that 0x7C900000 appearing on top of the stack.
The control flow soon jumps to 0x401077 and 0x401078. It soon follows that at 0x401070, ECX now has value 0x7C90000 (the DLL base). Now consider the instruction 0x40107D:
MOV EAX, DWORD PTR DS:[ECX+3C]
Recall that the beginning of a PE file is the DOS header (which is 64 bytes) and the last 4 bytes of the DOS header contains the location of the PE header (offset relative to the DLL base) [see Section 2]. Hex value 0x3C is decimal value 60! So we now have EAX containing of PE offset. Observing the registry pane, we have EAX = 0xE0. We then infer that PE header is located at 0x7C9000E0 (which is 0x7C900000 base + offset 0xE0).
Now observe instruction at 0x401087:
MOV ESI, DWORD PTR DS:[EAX+78]
Note the offset 0x78, its decimal value is 120. From Figure 1, we can soon infer that offset 0x78 is the address of the EXPORT table data entry in the IMAGE_DATA_DIRECTORY of the optional header. Thus, ESI now contains the entry address of the export table (offset relative to DLL base) ! After instruction at 0x40108c, Its value is now 0x7C903400 (starting address of EXPORT TABLE).
5. Challenge of the Day
We have demonstrated to you some basic analysis techniques to reverse engineer the malicious logic. Now your job is to continue our analysis and explain what the Max++ malware is trying to do. Specifically, you can follow the road-map below:
(1) What does function 0x004138A8 do? What are its input parameters?
(2) Which data fields of the export table are the instructions between 0x4010AD and 0x4010C4 accessing?
(3) Explain the meaning of EDX*+C in the instruction at 0x4010BB.
(4) Explain the logic of 0x4010CB to 0x4010F6.
(5) What is the purpose of the loop from 0x401103 to 0x401115?
(6) What does function 0x40165E do? What are its input parameters?
(7) Explain the code between 0x401117 and 0x40113E.
References
1. Goppit, "Portable Executable Format - a Reverse Enginnering View", v1(2), Code Breakers Magzine, January 2006.
2. An online copy of winnt.h, Available at http://source.winehq.org/source/include/winnt.h

Hi,
ReplyDeleteI really have read couple of articles over pe executable file format to understand it more in depth. But yup i am agree, that you made few points more clear. Thanks for that.
Dr,
ReplyDeleteYou made a VERY COMPREHENSIVE tutorials on malware analysis. but hardly to see any of your publication in malware problems.
Why is that?
I saw your PhD thesis also was in different topic. Just curious.
Your tutorials are very helpful. Thanks!!!
Good article
ReplyDeletechallange 1 : (future refrence)
ReplyDelete1. Name array, find the name and its index, for ex- (1)st function is CsrAllocateCaptureBuffer
2. Ordinal array(2 byte only), get the index ordinal , ex -(1)st ordinal is 0008
3. function address array, find the address using ordinal value , ex - (0008) i.e 8 th position which is = 0001eb58
finally add offset to base address.
what is meant by image base address, virtual address and relative virtual address ?
ReplyDeletewhat i know is, in the demand paging cpu generates a virtual address which contains page number address+ offset d from that we check page table and then map to the appropriate frame in main memory and calculate physical address by (frame no-1)* page size + d
but when i have read about PE file format its very different
what i found is virtual address= image base + relative virtual address offset
can anyone please explain this why its different ?
Audio typing services look like the traditional dictating services, digital audio services take away the problem of motor sound, thus, improving the quality. typing services offered
ReplyDeleteI think this is an informative post and it is very useful and knowledgeable. therefore, I would like to thank you for the efforts you have made in writing this article. If you are looking for antivirus security for your PC and any other digital devices than. Visit at my sites :- norton.com/setup
ReplyDeleteNice blog!!!!!!!.
ReplyDeleteReverseEngineering
Thankyou so much for spending time to write this blog article, i must say you are a excellent and talented blogger, I Found This Article To Be Very Infromative and Helpfull, please keep sharing such amazing blogs I am a Accountant from United States of America, Washington Dc, and I Love to read and Write Blog.
ReplyDeleteSome Of My Web Blogs Awesome Blog Post Please Feel Free to Check Out My Blog you will find the process of norton software installation with step by step instrcutions and much more.
Keep Sharing will come back to read more,
Click to Process
norton.com/setup download and install
norton.com/setup enter product key
www.norton.com/setup
login.norton.com
my.norton.com
norton.com/setup
norton.com/setup activate
norton.com/setup install
norton.com/setup help
norton.com/setup renewals
norton.com/enroll product key
Aeromexico Book A Flight Thanks for the information provided by you it’s really great to help from your side but I got the complete solution from the mentioned site
ReplyDeleteGet the very easiest & simple way to book your Frontier Airlines Reservations, our customer service 24*7 available for customer support, you can easily book your flight tickets by visiting our website.
ReplyDeleteSo nice to discover someone with a few unique thoughts on this issue.
ReplyDeleteSeriously.. thank you for starting this up. This site is something that’s needed on the web, someone with a little originality!
Here is the link of
https://softserialskey.com/simplify3d-crack/
Download free from here☝
ReplyDeleteAre you prepared to share more about this post?
I get the feeling you could be downplaying some of your more controversial opinions, but I for one, love reading them!
https://softkeygenpro.com/adobe-xd-cc-crack/
To be honest I found very helpful information your blog thanks for providing us such blog PS-W vs SS-W Dream11 Team Prediction
ReplyDeleteQatar Airways Reservations
ReplyDeleteBritish Airways Reservations
Hawaiian Airlines reservations
American Airlines Reservations
Southwest Airlines reservations
Sun Country Reservations
ReplyDeleteAir Canada Reservations
Copa Airlines Reservations
Allegiant Airlines Reservations
Jetblue Airlines Reservations
Hawaiian Airlines Reservations
Spirit Airlines Reservations
Singapore Airlines Reservations
ReplyDeleteAmerican Airlines Booking
United Airlines Booking
Delta Airlines Booking
Aeromexico Reservations
Frontier Airlines Reservations
British Airways Reservations
ReplyDeleteLufthansa Reservations
Air France Reservation
KLM Reservations
Eva Airlines Reservations
Icelandair Reservations
qantas airlines reservations
ReplyDeleteMokulele Airlines Reservations
Cathay Pacific Reservations
Finnair Reservations
Interjet Reservations
Alitalia Reservations
Thanks for your article. It was interesting and informative.
ReplyDeleteHere I also want to suggest your reader who usually travels one place to another they must
visit Airlines Gethuman that offer best deals to book your seat on Delta Airlines Reservations.
So do hurry and avail the best deals and get rid of to check different websites for offers.
Spirit Airlines Booking Number
Spirit Airlines Morning Flights
Spirit Airlines Reservation Number
Spirit Airlines Reservations
Spirit Airlines Support Number
Lufthansa Airlines Customer Service Number
ReplyDeleteLufthansa Airlines Reservation Number
Lufthansa Airlines Manage Booking
Lufthansa Airlines Manage Booking Number
Lufthansa Airlines Booking Number
Lufthansa Airlines Cancellation Number
Lufthansa Airlines Support Number
Get the lowest fares on Domestic and International Lufthansa Airlines Booking Number with the best discount & offers. Contact us at Lufthansa Airlines Reservation Number 1-888-826-0067.
Get the lowest fares on Domestic and International Southwest Airlines Booking Number with the best discount & offers. Contact us at Southwest Airlines Reservations Number +1-888-539-6764.
ReplyDeleteAir Travel Mart
Southwest Airlines Reservations
United Airlines Reservations
American Airlines Reservations
Qatar airways reservations
Delta Airlines Reservations
I am happy to be here and this wonderful blog. I have found here lots of important information for my knowledge I need. Thanks for sharing this amazing post.
ReplyDelete
ReplyDeleteSouthwest Airlines support Number
Southwest Airlines Booking Number
Southwest Airlines Reservation Number
Spirit Airlines Booking
ReplyDeleteDelta Airlines Booking
American Airlines Book a Flight
Frontier Airlines Book a Flight
Air Canada Booking
Southwest Airlines Booking
United Airlines Book a Flight
Alaska Airlines Book a Flight
KLM Airlines Booking
Best method to create your primevideo com mytv account through the activation process by primevideo.com/mytv. You need to follow the instructions to activate www.amazon.com/ mytv login
ReplyDeleteYou need to know about this blog that this content is very nice to read for all points of view. I find the Frontier Airlines New Year Flights Deals from the Fares Match to manage my Chicago Booking.
ReplyDeleteThank you for the relevant post and sharing with us....
ReplyDeleteHow to Send Email From HP Printers through Gmail
(Solved) Method of How To Reset HP 2600 Printer Password
Create The Ultimate SEO Traffic Generation Code in 2021-22
Unable to login amazon prime video go to link in your web browser that is www.amazon.com/mytv login. Login to your prime video account using your prime video login credentials. After that enter the activation code you have on your screen .Devices Compatible with Prime Video. Exclusive content and Amazon Original series Enjoy exclusive movies and TV shows on your device.
ReplyDeleteAeromexico Telefono
ReplyDeleteNumero De Telefono De Aeromexico
Telefono De Aeromexico
Aeromexico Telefono USA
Aeromexico Telefono Mexico
Telefono De Aeromexico En Espanol
Aeromexico Official Site
Aeromexico Telefono USA Mexico
Antiviruses Keep Your System Safe
ReplyDeleteBest Feature Of Malwarebytes Is Its Detection
Norton antivirus is the top notch antivirus service
ReplyDeleteWhy is Malwarebytes not scanning Windows PC?
Copa Airlines Telefono
ReplyDeleteVolaris Telefono
Telefono De United Airlines Espanol
united airlines customer service Spanish
delta baggage
ReplyDeletedelta baggage fees
delta international baggage
delta airlines customer service
Delta Airlines Flights
Delta Airlines book a flight
Delta Airlines telephone number
delta airlines mobile
Delta Airlines reservations
flights to chicago
flights to europe
ReplyDeleteflights to las vegas
Flights To Orlando
flights to denver
flights to florida
flights to miami
Flights To puerto rico
flights to detroit
flights to hawaii
Flights To new york
I like what you guys are up too. Such clever work and reporting! Keep up the superb works guys I have incorporated you guys to my blogroll. I think it’ll improve the value of my web site :).
ReplyDeleteWindows 10 Printer Offline error
ReplyDeleteWPS Connections in HP Printers
Canon Printer Service Tool
Steps To Resolve HP Printer Troubleshooting
Whether you are facing difficulty in booking your flight or need help with your flight cancellation or want information about the refund policy, the team members at Delta Airlines Amsterdam Office are informative and experienced to handle all your issues and concerns
ReplyDeleteProtect your brand name or logo through trademark registration at very affordable prices. Hire Regalguru and get your brand name registered without any hassle. Regalguru offers the best services for registration of trademark in Delhi.
ReplyDeleteFree Trademark name search India
Thank you for the relevant post.
ReplyDeletebusiness listing USA
Norton includes layered protection technology for your devices. Talk to our expert technicians for Norton family login or visit our website - www.norton.com setup.
ReplyDeletegreat share
ReplyDeletehttps://higherlovewellness.com/
hp.com/123 is the best answer to technical support. State your problem now and find the solution immediately. Call HP Printer Support Toll Free Number and talk to our experienced technician's team.
ReplyDeleteCar part junction has offered many, used car spare parts online. Now replace the defective parts of your car and give your car a new look and life, now you can buy used auto engine at the cheapest price.
Norton set up is one of the most popular antivirus which is highly known for protecting device and giving a one stop security solution to all the people worldwide. If you have any questions, visit - norton.com/setup download and install.
Now change the defective parts of your car and purchase used auto part, You can buy used car engine at the cheapest price.
ReplyDeleteCall us for any type of Norton internet security login and setup problems and visit :- norton.com/setup download and install.
If you are facing any kind of problem in your HP printer then you can call HP Printer Support Contact Number USA or visit our website - 123.hp.com/setup.
The description of Windows 12 ISO 64-bit 32-bit Download is included on a sheet of paper, there you can read, for example, that this operating system starts three times as fast as the original Windows 10 and is also ideal for gamers who use Steam and Nvidea drivers (sic !) use. It is emphasized several times that Microsoft does not access any data here and does not do business on the back of the user through advertising.
ReplyDeleteDownloading FuboTV means that you can get an opportunity of enjoying a wide range of live sports and entertainment content! You may get 100+ channels with 500 hours of cloud DVR storage. In addition to this, you also get to stream cumulatively on different devices. The streaming application provides primetime shows and family-oriented movies as well.
ReplyDeletefubo.tv/Connect
Japan Airline, Just amazing — they’ve never been late for me, but Japan airlines ticket cancellation policy is a little bit difficult to understand. After searching so much about the its policy, finally, I got a solution by {Airlinespolicy.com}. They have crisp, short, and relevant information about charges, modification, cancellation, check-in, Baggage, and Pet policy. They helped me a lot during the harsh Covid-19 time. I am very thankful to the team of airlinespolicy.
ReplyDeleteMy experience says that not all conditions are good to travel by air sometimes conditions caused by nature, and and in some cases by our issues it brings about change or retraction of the booked Air ticket. I generally really like to go with Lufthansa Airlines since it's straightforward the Lufthansa airlines ticket cancellation offer substantially more adaptability. I'm very thankful to the team of Airlinespolicy.com, who guide me about Lufthansa Airlines and its all policy in detail.
ReplyDeleteI am a frequent traveler, my personal travel experience says that not all conditions are good to travel by air sometimes conditions caused by nature, and in some cases, by our issues, it brings retraction of the booked Air ticket. I generally really like to go with Etihad Airlines since it's straightforward the Etihad flight ticket cancellation policy offer substantially more adaptability. I'm very thankful to the team of Airlinespolicy.com, who guide me about Etihad Airlines and its all policy in detail.
ReplyDeleteNikatby Services develop the mobile recharge software for the desktop and mobile devices. We are the best
ReplyDeleteMobile Recharge Software Company in India.Nikatby Services mobile Recharge software development Company.
flights to houston texas
ReplyDeletecheap flight to houston texas
las vegas cheapest flights
united airlines manage bookings
united airlines manage bookings
american airlines manage bookings
delta airlines manage bookings
british airways customer service 24*7
This is a great post I seen because of offer it. It is truly what I needed to see seek in future you will proceed after sharing such a magnificent post.
ReplyDeleteNikatby Services and Technologies Pvt Ltd, is a digital and FinTech company based in Noida. It provides multiple services to merchants and retail counters such as money transfer/remittance, mini ATM,etc, we are best company for Micro ATM Service Provider in noida,
ReplyDeleteIndia.
First step is opening the website, www.aa.com. This is the official website of American Airlines. Once on the site, locate “Find Your Trip” tab and click on it. American Airlines Manage Booking page will be displayed on your screen.
ReplyDeleteeva air flight change policy Passengers can request for the same day flight change through many available options provided by Eva Air. The passenger requires to pay Eva Air Ticket Change Fee for that. The change fee maybe 50 USD to 300 USD as per the ticket type and route of the passenger.
ReplyDeleteBest Mobile Recharge Software company in Noida. We provide Mobile Recharge Software Service and Multi Recharge Software that makes your life easier by giving the facility of mobile, DTH recharge instantly anywhere. We are best Mobile Recharge API Provider in India Noida.
ReplyDeleteNikatby Services is the Leading DTH Recharge API provider in India , we are providing Best DTH Recharge API services in India. Our DTH recharge API is available for all the major DTH operators such as Dish TV, D2H, Big TV, Tata Sky, Videocon, Sun Direct, Airtel Digital TV, etc.
ReplyDeleteVardman Industries is one of the leading global natural stone suppliers and exporters of Indian stones, such as granite, marble, sandstone , Limestone , Porcelain etc . we are suppliers and exporters premium quality Indian natural stones.
ReplyDeleteLikert scale is a five (or seven) point scale which is used to allow the individual to express how much they agree or disagree with a particular statement. Learn more: https://ppcexpo.com/blog/how-to-analyze-likert-scale-data
ReplyDeleteNice Blog. Thanks for sharing with us. Such amazing information.
ReplyDeleteOnly Blog
Guest Blogger
Guest Blogging Site
Guest Blogging Website
Guest Posting Site
Runjhun Export is one of the leading global natural stone suppliers and exporters of Indian stones , such as granite, marble, sandstone , Limestone , Porcelain etc . we are Suppliers and exporters premium quality Indian natural stones.
ReplyDeleteThank you very much for your time and attention in our conversation of this afternoon. Reported calls USA And also visit Mobile Prices Bangladesh
ReplyDeleteYou can modify orchange flight without fee in Delta Airlines. Dug deeper to find ways like making changes within 24 hours of booking and other hacks to save yourself from paying cancellation or change fee for making any voluntary
ReplyDeletemodifications. Call 1-888-441-7259.
Runjhun Export is leading manufacturer and exporter of White Mint sandstone in India, we are offering this sandstone in finishes like honed, polished, bush-hammered, tumbled, brushed, sandblasted and sawn.Mint White Natural Sandstone also called as Tinted Mint.
ReplyDeleteRunjhun Export is leading Tandur Yellow Limestone Supplier Manufacturer and Exporter in India .Buy high quality Tandur Yellow Natural Limestone by Runjhun Export . Tandur Yellow Limestone is a high quality limestone that is mostly used in Flooring, Floor Pavement of commercial complexes, Interior decoration like wall cladding, countertops, etc.
ReplyDeleteDelta airlines bookings
ReplyDeletejetblue airlines tickets
Aeromexico Airlines
Alaska Airlines bookings
American Airlines Reservations Phone Number
ReplyDeleteamerican airlines flights reservations
American Airline Flights Reservations
American Airlines Flights Reservations
American Airlines Flights Reservation
American Airline Flights Reservations
Vardman Industries is one of the leading Mint sandstone from Certified Exporter Supplier and manufacturer in india. A variety of raw, beautiful, sandblasting and antique surface finishes is what this mint sandstone is blessed with. To furnish your interiors, Call Today!!
ReplyDeleteIt is the best way to save your money, and you will get several tips to skip the unwanted fee. You can visit its official website to check out the Qatar Airways policy.
ReplyDeleteSpirit Airlines Cancellation policy
Turkish Airlines Cancellation Policy
Alaska airlines cancellation policy
Qatar airways cancellation policy
Hawaiian airlines cancellation policy
If you want to get your hands on the most affordable flight ticket with luxurious facilities, then you should make an Alaska airlines booking.
ReplyDeleteDelta airlines booking
Alaska airlines booking
Frontier airlines booking
British airways booking
delta airlines book a flight
It’s really nice and meaningful. It’s really cool blog. Thanks for sharing and please update some more information here. Students need to gain relevant ideas about the Courses after 12th. The changing time has provided various career segments through which they can see their future. However, a substantial decision can be taken by evaluating one's own likings towards the career field. Students can select the courses after completing their 12th as per the subject they had taken in the 12th itself from a career point of vi
ReplyDelete
ReplyDeletelearn more
learn more
learn more
learn more
learn more
learn more
learn more
Delta Airlines: Experience the Best Flying Journey - Book Cheap Flight Tickets to Anywhere - Services You Will Love
ReplyDeleteWith the help of online flight booking, you can go for online airline booking and also do flight tickets booking at your fingertips. Online airline booking save your time and money with providing cheap flight tickets booking.
If you have a Delta Airlines flight booking and wish to manage your booking, you can do so very easily and quickly online through Delta Airlines Manage Booking.
Delta Airlines: Experience the Best Flying Journey - Book Cheap Flight Tickets to Anywhere - Services You Will Love
ReplyDeleteWith the help of online flight booking, you can go for online airline booking and also do flight tickets booking at your fingertips. Online airline booking save your time and money with providing cheap flight tickets booking.
Delta Airlines: Experience the Best Flying Journey - Book Cheap Flight Tickets to Anywhere - Services You Will Love
ReplyDeleteWith the help of online flight booking, you can go for online airline booking and also do flight tickets booking at your fingertips. Online airline booking save your time and money with providing cheap flight tickets booking.
If you have a Delta Airlines flight booking and wish to manage your booking, you can do so very easily and quickly online through Delta Airlines Manage Booking.
In this article, the user describes about the Spirit Airlines Reservations & how to get flight tickets instantly. So here passengers can learn about the procedure of online tickets booking of Spirit Airlines & use the official online portal of Spirit Airlines.
For most trips, airfare is the most expensive part of the trip. While prices for transatlantic flights have gone down in recent years, they can still put a sizeable dent in any travel budget. Whether you’re a budget solo traveler or a family looking to vacation abroad, finding a cheap flight deal can be what makes or breaks your trip.
ReplyDeleteallegiant airlines tickets
Everyone likes to travel by plane with family and friends, if you travel at the lower price, you will be more adventurous.
ReplyDeleteThis year, American Airlines launched heaviest and craziest travel discount, allowing you to save even more. If you subscribe to the newsletter or reminder a few months ago, you will receive exclusive last minute offers and discounts from the airline on your registered email ID.
american airlines reservations
This comment has been removed by the author.
ReplyDeleteNice Post! Thanks for sharing!
ReplyDeleteCustom embroidery services
Screen printing company
Hello, my name is madison bailey from the United States, and I’d like to share some information about Organic supplements in the UK. Troo Health products are EFSA approved claims High strength curcumin turmeric is one of the products manufactured by our firm. Organic supplements in the UK are used to solve different health problems such as skin and digestive issues. It gives major benefits to our body and brain.To know more visit our website.
ReplyDeleteYour data is exceptionally interesting. If you need to get the detailed data about Hawaiian airlines 24 hour cancellation policy and want to identify limits on cancellation of booked air tickets, visit our site. We have all the necessary, important, and crisp updated information about Hawaiian airline's cancellation policy.
ReplyDeleteOPAUTOCLICKER
ReplyDeleteGSAUTOCLICKER
MURGEEAUTOCLICKER
MINECRAFTAUTOCLICKER
ROBLOXAUTOCLICKER
Be the part of Adidas and get amazing gift voucher and coupon code
ReplyDeleteAdidas Coupon Code
Adidas Voucher Code
Adidas Promo Code
Adidas Voucher Code 2021
Adidas coupon code Singapore
TripiTravels provide low-fare international flights and exclusive flight discounts for extra saving!
ReplyDeleteCape Airlines international reservations
Allegiant Airlines international reservations
JetBlue Airlines international reservations
Grab offers on international flights at TravelQart, a flight dedicated platform and the best airline booking portal.
ReplyDeleteSouthwest Airlines international reservations
Japan Airlines international reservations
AirlineTicketWorld is a one-stop destination to compare the prices of 100+ airlines.
ReplyDeleteBook affordable international flight tickets of top-notch airlines.
JetBlue Airlines international reservations
Allegiant Airlines international reservations
This comment has been removed by the author.
ReplyDeleteSpirit Airlines Vacation Packages
ReplyDeleteSpirit Airlines Vacation Packages
Spirit Airlines Reservations Customer Support
Spirit Airline Manage Booking
Spirit Airline Check-in
Spirit Airline mobile App
There’s lot of posts on the net that claim to explain how to book cheapest flight tickets. Most of them simply advise you to book early while others subtly try to promote their own booking sites/services. Others propose booking on particular day of the week and time of the day. Lot of people approach me stating they need to go somewhere and if I have a way to get them cheap tickets. I don’t have any secret sauce for getting cheap tickets particularly when someone has a date and destination fixed and doesn’t have any flexibility. On the other hand if you’re flexible with date and destination, there’s a lot that can be done to fly at much cheaper price.
ReplyDeletejetblue airline flights tickets
Vardman Industries is one of the leading Kota Brown Polished Limestone Exporters and Suppliers From Kota India. we are offering premium quality range of natural stones namely Kota brown polished / honed that are available in different size ranges.
ReplyDeleteA lot of people arise to me and say they want to move someplace if I actually have a manner to get them to buy reasonably-priced tickets. I don't have any secret to getting reasonably-priced tickets, specifically while a person has set the date and vacation spot and has no flexibility. On the alternative hand, in case you are flexible about dates and destinations, there are numerous matters you may fly at a less expensive price.
ReplyDeleteKLM Royal Dutch Airlines
ReplyDeleteCathay Pacific airlines reservations number
Allegiant Airlines Online Booking
Allegiant Airline Reservations Number
Allegiant Airlines Phone Number
Allegiant Airlines Online Booking
Cathay Pacific Flight Booking
JetBlue reservations phone number
Airline Low Cost Flight Tickets
Spirit Airlines offers multiple ways to book tickets. The process of Spirit Airlines reservations is quite easy and you can make it online with ease of mind. There are three ways to make reservations with Spirit Airlines by Its official website, Mobile app, and customer care number.
ReplyDeleteRead Also : How to make reservations with Spirit Airlines Spanish Telephone?
aeromexico airlines manage booking
ReplyDeleteAllegiant Airlines Reservations
ReplyDeleteAmerican Airlines Booking for Flight Reservation
Contact Alaska Airlines Representative
What to Do If You Are Facing Cash App Limit Problems?
ReplyDeleteTo have the right kind of support regarding Cash App Limit, you should immediately get in touch with the professionals .Here, they will provide you with the best possible solutions so that you will be able to increase the limit of your Cash App account without having to face any issue regarding the same.
"Vardman Industries Leading Rainbow Sandstone Exporter Supplier and Manufacturer in India .we are offering Indian sandstone paving slabs, paving stone, tiles, steps, flagstone, and risers at competitive prices. Purchase top quality rainbow sandstone paving slabs in competitive prices, processed at stone factories, from ISO-qualified Indian sandstone manufacturer.
ReplyDeleteKhatu Rainbow Sandstone, with a blend of beautiful colors, this sandstone has always proven its durability, strength and toughness. What are you waiting for?"
Delta provides amazing facilities to the passengers during the travel. Delta Airlines offers three types of cabin classes First class, Business class, and Economy class. If you are planning to go via air, then book with Delta Airlines Reservations is the best option for you. It provides luxury comfort during travel. If you have already booked your flight with Delta Air and want to make some changes to it, Delta Airlines Manage Booking is the best way to make changes in existing reservations.
ReplyDeleteBook Spirit Airlines Reservations with Goskylinetravel. Spirit knows that lots of customers want low fares. Spirit Airlines is the leading Ultra-Low-Cost Carrier in the United States, the Caribbean, and Latin America. If you have already booked your flight with Spirit Air and want to make some changes to it, Spirit Airlines Manage Booking is the best way to make changes in existing reservations.
Vardman Industries Leading Rippon Buff Natural Sandstone Manufacture and Suppliers In India.The Rippon Buff Natural Sandstone looks like an authentic, natural and appealing blend of colors. We are supplier of Rippon Buff sandstone Paving Slabs which is also extracted from the quarries in Kota. This sandstone is also known as Earlston Rippon Buff and is hand cut and tumbled to provide an international beautiful rustic and aged finish.
ReplyDeleteMake sure to contact Spirit airlines reservations Sales and Guest Services directly at (+1-888-801-0869) if you need assistance with modifying or canceling your reservation, using a reservation credit or travel gift card, or other general inquiries. Alternatively, Spirit airlines customer service number you can text us at 48763, or call us at +1-888-801-0869 on call 24 hours a day, 7 days a week.
ReplyDeleteSpirit Airlines Reservations
Wow, such an awesome blog you have written there and you and I get exactly what information I am looking for, in the third paragraph you put amazing effort to explain the theme of the content. As a content writer, I can understand efforts because when students ask me for sitxglc001 assessment answers, I do the same.
ReplyDeletemaximum 20 websites in a server, isn't fast or secure? there is no doubt it is most secure and fast, visit https://pectel.xyz/Web-Hosting.html
ReplyDeletehttps://ext-5842695.livejournal.com/911.html
ReplyDeleteVardman Industries is one of the leading Kandla Grey Sandstone Exporters and Suppliers From Kota . Kandla Grey Smooth Sandstone extracted from the city of Kota, Rajasthan. For some discerning customers, it can be found in two different shades that is Light Grey Sandstone and Dark Grey Sandstone.
ReplyDelete"Vardman Industries Leading Rainbow Sandstone Exporter Supplier and Manufacturer in India .we are offering Indian sandstone paving slabs, paving stone, tiles, steps, flagstone, and risers at competitive prices. Purchase top quality rainbow sandstone paving slabs in competitive prices, processed at stone factories, from ISO-qualified Indian sandstone manufacturer.
ReplyDeleteKhatu Rainbow Sandstone, with a blend of beautiful colors, this sandstone has always proven its durability, strength and toughness. What are you waiting for?"
ReplyDeleteSpirit change name on flightAre you facing problems with Spirit changing names on flight? Don't worry. Here you will instantly fix these problems within a few minutes
Vardman Industries is one of the leading Limestone Manufacturers and Supliers in India . we are certified Indian Natural Limestone, exporter, supplier, and a manufacturer in India, brings you a specific range of limestones.
ReplyDeleteLimestones are sedimentary rocks that include an amazing blend of calcium carbonate minerals, calcite and chemical composition of CaCo3. Limestones are generally formed in the clean, calm, warm, and shallow environment that inclines us towards the deep marine water containers like Pacific Ocean Islands, Persian Gulf, Indian Oceans, etc.
Vardman Industries is one of the leading sagar black sandstone provider in indiaBesides, the consistency and reliability of Sagar Black Indian sandstone are highly common in the whole Indian natural sandstone categories.
ReplyDeleteSagar Black Sandstone from India is also known as Carbon Black Sandstone, Black Sandstone, Antique Grey Sandstone, Indian Black Sandstone, Sugar Black Sandstone, Kalahari Black Sandstone, Mountain Black Sandstone, Charcoal Black Sandstone, Midnight Black Sandstone, Titanium Black Sandstone, Premium Twilight Sandstone in International Market.
"Vardman Industries is one of the leading Tandur Grey Limestone Paving provider in india Besides, the consistency and reliability of Tandur Grey Limestone are highly common in the whole Indian natural sandstone categories.
ReplyDeleteLime Grey or Tandur Grey Limestone is limestone that holds a bluish-grey color to its surface with some white-colored soft veins that make this stone one of the most high selling stones in the Indian natural stone industry. "
"Vardman Industries is one of the leading sagar black sandstone provider in indiaBesides, the consistency and reliability of Sagar Black Indian sandstone are highly common in the whole Indian natural sandstone categories.
ReplyDeleteSagar Black Sandstone from India is also known as Carbon Black Sandstone, Black Sandstone, Antique Grey Sandstone, Indian Black Sandstone, Sugar Black Sandstone, Kalahari Black Sandstone, Mountain Black Sandstone, Charcoal Black Sandstone, Midnight Black Sandstone, Titanium Black Sandstone, Premium Twilight Sandstone in International Market. "
it was a nice article and very helpful
ReplyDeleteQuality Control Training in Chennai
Appium Training in Chennai
Thank you for sharing this useful content and I really get some useful information from this content.
ReplyDeleteigoal
"Vardman Industries is one of the leading Limestone Manufacturers and Supliers in India . we are certified Indian Natural Limestone, exporter, supplier, and a manufacturer in India, brings you a specific range of limestones.
ReplyDeleteLimestones are sedimentary rocks that include an amazing blend of calcium carbonate minerals, calcite and chemical composition of CaCo3. Limestones are generally formed in the clean, calm, warm, and shallow environment that inclines us towards the deep marine water containers like Pacific Ocean Islands, Persian Gulf, Indian Oceans, etc."
This comment has been removed by the author.
ReplyDeleteVardman Industries is one of the leading Natural stone manufacturers and supplier in India . we are providing Natural Indian stones , such as granite, marble, sandstone , Limestone , Porcelain etc . we are suppliers and exporters premium quality Indian natural stones.
ReplyDeleteDelta Airlines has always been one of the most authentic and reliable airlines across the globe. They are dedicated to providing the best facilities to their passengers, but they are quite strict about their strict rules and regulations. If the person traveling with Delta doesn't have the correct credentials and their name in their respective boarding pass, they might be facing problems with flight access. To avoid such a problem, it provides a Delta Airlines Name Change Policy.
ReplyDeleteWould you like to place an order? The finest quality of Original pukhraj stone 7.25 ratti price at unbeatable. Shop now and experience the difference!
ReplyDeleteVenacavadesigns, a creative powerhouse in the world of graphic design, is known for its innovative and visually stunning creations. With a keen eye for aesthetics and a commitment to delivering unique solutions, Venacavadesigns transforms ideas into captivating visual experiences. Whether it's crafting eye-catching logos, designing striking marketing materials, or conceptualizing visually appealing websites, Venacavadesigns seamlessly blends artistry with functionality. The team at Venacavadesigns is dedicated to pushing the boundaries of design, creating a distinct identity for each project they undertake. Explore the world of graphic design through the lens of Venacavadesigns and witness the fusion of creativity and expertise that defines their signature style
ReplyDeleteVisit VenaCavaDesigns.com
Welcome! I'm Michael Smith from Offshore Gateways. Our focus on Internet Merchant Accounts ensures that your online transactions are secure and efficient. Trust us to Set Up Merchant Accounts tailored to your business needs. Explore our website for insights into how we can optimize your payment processes.
ReplyDeleteOffshore Gateways Merchant Accounts | Merchant Accounts | Merchant Accounts Online | Internet Merchant Accounts | Set Up Merchant Accounts | Merchant Account Fees | Open Merchant Account Online
Howdy folks, Blue Smith here, representing Payments Clarity, your trusty companion in navigating the world of payments. If you're gearing up to tackle the challenges of Offshore high risk payment gateway, you're in the right place. Let's make it smooth sailing together with our wealth of experience and specialized solutions. Check out our Offshore online payment processing options, meticulously crafted to meet your needs and exceed your expectations. With our Offshore payment service provider expertise, you can rest assured that your transactions are in good hands. So, why wait? Let's embark on this journey together and unlock the potential of your business.
ReplyDeleteOffshore Company Registration | Offshore payment processors | Offshore high risk payment gateway | Offshore payment gateway high risk | Offshore online payment processing |
Offshore payment service provider | Offshore merchant payment services
Website looking a bit dull? Not getting the traffic you hoped for? Don't worry, I'm here to help! I'm Sai Pallavi from NWSPL, and we excel at creating eye-catching websites that drive results. Our Web design development services in Delhi are tailored to suit your business needs, whether you're an e-commerce store or a service-based company. Let's turn your website into a powerful sales tool together!
ReplyDeleteWebsite Design Development | Web Design Development Services In Delhi | Web Design & Development Company In Delhi | Web Development Company In Delhi | Website Designer In Delhi | Creative Website Agency In Dwarka | Web Design & Development Agency In Dwarka Delhi | Professional Web Design And Development Services In Dwarka | Website Designing Services In Delhi | Web Design Company Near Dwarka
Name: Aap Indian Restaurant | Indian Restaurant | Cincinnati OH
ReplyDeleteAddress: 6430 Glenway Ave, Cincinnati, OH 45211
Phone: +15138327448
Finding a family-friendly Indian Food Restaurant In Cincinnati OH, is a breeze. These establishments not only serve delicious food but also provide a warm and welcoming atmosphere that’s perfect for family gatherings. Our Aap India restaurant offer a variety of dishes that cater to both adults and children, from mild curries to sweet treats like gulab jamun. With spacious seating and attentive service, they ensure a delightful dining experience for all ages.
Name : Rajaji Curry House Indian Restaurant
ReplyDeleteAddress: 2603 Connecticut Ave NW #2634, Washington, DC 20008
Phone: +12022657344
For the best Indian food in Washington, DC, Raja Ji is the perfect spot. Our restaurant offers a wide range of traditional Indian dishes, from rich butter chicken to spicy vindaloo and aromatic biryani. Each dish is crafted with fresh ingredients and authentic spices to ensure an unforgettable dining experience. Come to Raja Ji in Washington, DC, and discover why we are a favorite among Indian food lovers.
¿Necesitas ayuda con tu vuelo en cualquier momento? Copa Airlines ofrece servicio al cliente disponible las 24 horas del día. Llama al Copa Airlines teléfono 24 horas y recibe asistencia inmediata con tus reservas, cambios de vuelo y más. Estamos aquí para ayudarte las 24 horas del día.
ReplyDeletenúmero de teléfono de la aerolínea aeroméxico ?Para obtener asistencia o resolver dudas sobre tus vuelos, contacta con el número de teléfono de aeroméxico. Su equipo de atención está disponible para ayudarle con cualquier consulta relacionada.
ReplyDeleteA really Good post, I found a lot of interesting information here. Thanks for sharing.
ReplyDeleteI'm very glad to see such excellent information being shared freely out there
ReplyDeleteThis is the great contents that I ever seen, thankyou for sharing this post
ReplyDeleteI just want to say thank you for one million times to this fabulous article
ReplyDeleteMBBS in China offers high-quality medical education at affordable tuition fees, making it a top choice for international students. Chinese medical universities are recognized by the WHO and NMC, providing globally accepted degrees. With modern infrastructure, experienced faculty, and extensive clinical exposure, MBBS in China ensures excellent career prospects for aspiring doctors worldwide.
ReplyDeleteMBBS in Tamil Nadu is a preferred choice for medical aspirants due to its top-ranking government and private medical colleges. With excellent infrastructure, experienced faculty, and affordable fees, students receive quality medical education. MBBS in Tamil Nadu offers extensive clinical exposure, ensuring the best learning experience and career opportunities in the healthcare sector.
ReplyDeleteLinking is very useful thing.you have really helped D.
ReplyDeleteI want you to thank for your time of this wonderful read!!! D.
ReplyDeleteI really enjoy reading and also appreciate your work. D.
ReplyDeleteGreat Information sharing .. D.
ReplyDeleteI am very happy to read this article .. D.
ReplyDeletethanks for giving us go through info. D.
ReplyDeleteFantastic nice. D.
ReplyDeleteThanks to the coupons I saw on Super Savers Info, I was able to get some fantastic discounts on Adidas merchandise! I can't wait to show off my new shoes without feeling bad about going over budget. Thank you for the wonderful discovery.
ReplyDeleteRobinhood 24 hours contact number
ReplyDeleteRobinhood customer service 24 7
Robinhood toll free number
Robinhood phone number customer support
Robinhood tech support phone number
Robinhood contact number customer service
Your articulate and well-reasoned article served as an excellent benchmark. My profound gratitude.
ReplyDeleteGreat content! The information is straightforward and useful for anyone looking to save on sportswear. Definitely worth using our code RCZ10 along with the Sun And Sand Coupon Code.
ReplyDeleteWell explained. It’s easy to see why New Era Public School is counted among the best schools in Dwarka, offering quality education along with values and overall development.
ReplyDeleteMore Info:-
Best Schools in Dwarka Delhi
Dwarka schools
Best School in Dwarka