- Practice reverse engineering techniques.
- Understand basic checksum functions.
- Operating Systems.
- Computer Security.
- Assembly Language
1. Introduction
This tutorial answers the challenges in Tutorial 8. We explain the operations performed by Max++ which are related to export table. In this tutorial, we will practice analyzing functions that do not follow C language function parameter conventions, and examine checksum and encoding functions.
2. Lab Configuration
You can either continue from Tutorial 8, or follow the instructions below to set up the lab. Refer to Tutorial 1 and Tutorial 4 for setting up VBOX instances and WinDbg.
(1) In code pane, right click and go to expression "0x40105c"
(2) right click and then "breakpoints -> hardware, on execution"
(3) Press F9 to run to 0x40105c
(4) If you see a lot of DB instructions, select them and right click -> "During next analysis treat them as Command".
(5) Exit from IMM and restart it again and run to 0x40105c. Select the instructions (about 1 screen) below 0x40105c, right click -> Analysis-> Analyze Code. You should be able to see all loops now identified by IMM.
3. Analysis of Code from 0x40108C to0x4010C4
We now continue the analysis of Tutorial 8, which stops at 0x401087.
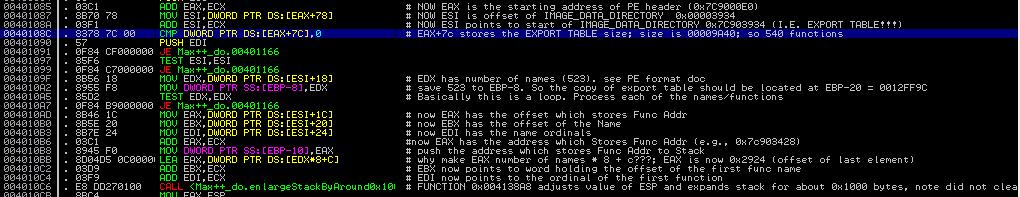 |
| Figure 1. Code from 0x40108C to 0x4010C4 |
Now let's observe the instruction MOV EDX, DWORD PTR DS:[ESI+18]. Note that ESI, after being set by instruction at 0x40108A, is now pointing at the export table. It contains value 0X7C903400 (which is the starting address of the export table). In Section 3 of Tutorial 8, we have given the data structure of the export table. From it, we can infer that offset 0x18 is the number of names. Thus, after the instruction is executed, EDX has the number of names (0x523) exported from ntdll.dll.
Using the same technique, we can infer that the subsequent instructions (0x4010AD to 0x4010C4) assigns registers EAX to EDI. We have:
EAX <-- offset (relative to 0x7C90000 starting of ntdll base) of the beginning address of the array that stores function entry addrsses
EBX <-- offset of the beginning of the array that stores the names of the functions
EDI <-- offset of the array that stores the name ordinals (as we mentioned earlier, to find the entry address of a function, we have to find its index of the function name in the function name array, and then use the index to find the ordinal, and then use the ordinal to locate the entry address in the array of function entry address)
We can verify the above analysis. Take EBX as one example, its value is 0x7C9048B4. The following is the dump of the memory starting from that address. Note that each element is the "offset of the name". So the first element is 0x00006790 (it actually means that the string is located at 0x7C906790), and similarly, the second string is located at 0x7C9067A9. Figure 3 now displays the contents at 0x7C906790 (you can see that the first function name is CsrAllocateCaptureBuffer).
 |
| Figure 2: Array of Function Names |
 |
| Figure 3: The Strings |
Now we proceed to the instruction at 0x004010C6 (see Figure 1). It calls the function located at 0x004138A8. Figure 4 shows a part of the function.
 |
| Figure 4: Function 0x004138A8 |
To figure out the input parameters of the function, we look at those registers that are READ before assigned. Looking at the instructions beginning at 0x004138A8, we soon identify that EAX is the input parameter, at this moment its value is 0x00002924. Recall that in Section 3, it contains the offset of the beginning of the array that contains function entry addresses, i.e., 0x7C902924 is the beginning of the array that contains function entry addresses.
Then starting from 0x004138A9, the next few arithmetic instructions seem to be rounding the value of ECX based on EAX. Now Figure 5 shows the second half of the function. There are two interesting instructions, first the instruction at 0x0041389A (it is to reduce the value of EAX by 0x1000 inside a loop), and then the instruction of 0x413893, it is to exchange the value of EAX and ESP.
So the eventual output is the ESP register, which has multiples of 0x1000 bytes (in our case 0x2000 bytes) reduced compared with its original value.
In a word, the function at 0x004138A8 expands the stack frame (recall the stack grows from higher address to lower address) by 0x2000 bytes. Why? It is used to hold the new export table, which is encoded!
Challenge 1 of the Day: where does the new export table start?
 |
| Figure 5: Second Half of Function 0x004138A8 |
We now proceed to analyze the code between 0x4010CB to 0x40113B. Note that the expanded stack now includes around 0x2000 bytes from 0x0012D66C. This is going to hold encoded export table. This encoded table (its format) is defined by the malware author himself/herself. Each entry has two elements and each element 4 bytes. The first element is the checksum of the function name, and the second is the function address. Later, the Max++ malware is able to invoke the system functions in ntdll.dll without resolving them using the export table of ntdll.dll, but using its own encoded table.
 |
| Figure 6. Code from 0x4010CB to 0x40113B |
Then there is a 2-layer nested loop from 0x004010F9 to 0x00401136. Let's first look at the inner loop from 0x401103 to 0x401110. Clearly, EAX is the input for this inner loop and note that EAX is pointing to the array of chars that represent the function name (at 0x004010FB). At 0x401110, EAX is incremented by one in each iteration of the inner loop. Clearly, the inner loop is doing some checksum computation of the function name. In the checksum loop, there are two registers being written by the code: EDX and ECX. If you read the code carefully, you will note that the value of EDX is overwritten completely in each iteration (note instruction at 0x401103). Only ECX's previous value affects its next value. Thus ECX must be the output and it saves the checksum!
Then the instructions from 0x401117 to 0x401133 are to set up the entry for the function. The instruction at 0x40111D (MOV DS:[EAX], ECX) is to save the checksum of the function to the first element, and then the instruction at 0x0040112B saves the function address as the second element.
Challenge 2 of the Day: Explain the logic of EDX+ECX*4 of the instruction at 0x00401122. Hint: study the use of ordinal numbers in export table.
5. Conclusion
Our conclusion is: Max++ reads the export table of ntdll.dll and builds an encoded export table for itself. We will later see its use.
6. Challenge of the Day
At 0x0040113E, Max++ calls 0x0040165E. Analyze the functionality of 0x0040165E.
thanks bro Dr. Fu's , good article.:-*:x
ReplyDeleteDr. Fu'S Security Blog: Malware Analysis Tutorial 9: Encoded Export Table >>>>> Download Now
Delete>>>>> Download Full
Dr. Fu'S Security Blog: Malware Analysis Tutorial 9: Encoded Export Table >>>>> Download LINK
>>>>> Download Now
Dr. Fu'S Security Blog: Malware Analysis Tutorial 9: Encoded Export Table >>>>> Download Full
>>>>> Download LINK A8
Very interesting behavior from Max++.
ReplyDeleteOrdinal value is actually the index of the AddressOfFunctions,The array is build from DWORD elements, This means that the value should be multiplied by four to get the RVA of a function.
ReplyDeleteDana Feigel
Dr.Fu, Excellent tutorials. Truly enjoyable.
ReplyDeleteHad 1 doubt . What is the significance of 7C902924? You have said that it points to beginning address of the array that stores function entry addrsses. Isn't 7C903428 pointing to that?
Thanks,
Jutsin
Your tutorial very good you solve many thing in codec thanks for share it engineering statement of purpose .
ReplyDeleteVery well written and easy to understand. Have taken our relevant point out of this blog and will surely pass it onto our configuration management team to put in a tool which does this metrics. Will be really helpful.
ReplyDeleteSource code security analysis
Thanks for your informative article, Your post helped me to understand the future and career prospects & Keep on updating your blog with such awesome article.
ReplyDeleteDocker online training
Docker certification training
Docker online course
Docker training course
ReplyDeleteThis is most informative and also this post most user friendly and super navigation to all posts. Thank you so much for giving this information to me.Docker training in Chennai.
Java training in chennai | Java training in annanagar | Java training in omr | Java training in porur | Java training in tambaram | Java training in velachery
Ashampoo WinOptimizer Download is the ultimate system optimization tool that offers a variety of tools for maintaining and optimizing your system, hard drive, security, and more.https://crackdaily.com/ashampoo-winoptimizer-download/
ReplyDeleteiExplorer Crack is the ultimate manager for iPhone, iPad, and iPod, and allows you to easily transfer music from any iPhone, iPod, or iPad to a Mac or PC and iTunes.iexplorercrack
ReplyDeleteDllKit Pro Crack allows you to repair DLL file errors and adjust the performance of your PC. The program can identify most problems with DLL files and repair them automatically.dllkitpro
ReplyDeletePhoneRescue Serial Key is an excellent data recovery tool that helps to recover lost or deleted data for your devices like iOS without any obstacle.phonerescuecrack
ReplyDeleteDriver Genius Keygen is the best software for Mac and Windows users to update their drivers in a professional way. It is full of professional features and makes them good tools.drivergeniuspro
ReplyDeleteBandicut Keygen is the basic software for cutting, splitting, and joining videos. The software interface is easy to use and easy to use.bandicutcrack
ReplyDeleteAvid Media Composer Activation Key is a software application for video and film editing.avidmediacomposer
ReplyDeleteLogic Pro X Crack is an astounding instrument for music stock. It likewise has the entirety of its data about creating and another form of data.logicprox
ReplyDeleteiTools Crack 4.4.5.8 Keygen is a little application that furnishes you with an interface to deal with your iOS gadgets by means of your Windows PC.itoolscrack
ReplyDeleteSave Wizard Crack is useful and easy to use. They use and copy their excess Play Station 4 to a large USB.savewizardd
ReplyDeleteBandicut 3.5.0.599 Crack is the fundamental programming for cutting, separating, and joining recordings.bandicutkeygen
ReplyDelete4K Video Downloader 4.12.5.3670 Crack is advanced and very easy to use Video Downloading Software. It allows you to download any video from the internet.4kvideodownloaderd
ReplyDeletePowerful and useful Sausage Fattener Crack plugin for archived music. It is a great plug-in tool to keep your music on file.sausagefattenercrack
ReplyDeleteThe Latest Version of NTLite Crack Free Download is a powerful Windows configuration and customization tool. It allows you to create an optimized version of Windows.ntlitecrac
ReplyDeleteMicrosoft Office Professional Product Key desktop applications. In most early versions, the Office included the three main areas of Office which are MS
ReplyDeleteWord, MS PowerPoint, and MS Excel.msoffice2013
CyberLink PowerDVD 20 Crack is an Award-winning most exhaustive film and media player for DVD, video, sound, and photograph playback.cyberlinkpowerdvd
ReplyDeleteNative Instruments Massive v1.5.5 Crack is one of the most proficient and broadly utilized applications in the field of the age of sound.nativeinstrumentsmassive
ReplyDeleteNative Instruments Massive v1.5.5 Crack is one of the most proficient and broadly utilized applications in the field of the age of sound.nativeinstrumentsmassive
ReplyDeleteMalwarebytes Crack is a reliable application to remove malware. This Anti-Malware helps detect and remove all types of malware such as worms, Trojans, rootkits, rogues, spyware, from your computer.malwarebytescrack
ReplyDeleteAdobe Photoshop CC Crack is a complete solution for professional images. It has a great idea to implement new intuitive tools to create graphics, films, three-dimensional projects.adobephotoshop
ReplyDeleteAuslogics Driver Updater Crack is a software program to update all drivers on your PC with just a few mouse clicks.auslogicsdriverupdater
ReplyDeleteSmartDraw Crack can be a very potent device for generating demonstration images. As a result of the application, it could generate complex graphics, a variety of calendars, diagrams, layouts, and much more.smartdrawcrack
ReplyDeleteI know this website provides quality based posts and additional stuff
ReplyDeleteBrilliant job!!
Do you know?
AOMEI Backupper Pro Crack: It is a powerful and easy to use backup and retrieval software with advanced features for data backup, synchronization, cloning, and restoration. Back up files, folders, partitions, hard drives, applications, and operating systems. With this feature, you can back up your important data, which can be restored if something goes wrong.
Hi there mates, good article and fastidious arguments commented at
ReplyDeletethis place, I am really enjoying by these.
Adobe XD CC
Thanks for sharing your thoughts. I truly appreciate your efforts and I will be waiting for your further write ups thank you once again.
ReplyDeleteGreat Article
ReplyDeleteCyber Security Projects
Networking Security Projects
JavaScript Training in Chennai
JavaScript Training in Chennai
The Angular Training covers a wide range of topics including Components, Angular Directives, Angular Services, Pipes, security fundamentals, Routing, and Angular programmability. The new Angular TRaining will lay the foundation you need to specialise in Single Page Application developer. Angular Training
I needed to thank you for this awesome read!! I certainly getting a charge out of each and every piece of it I have you bookmarked to look at new stuff you post.
ReplyDeleteGreat Work Keep it up! Sure Cuts A Lot Pro Crack
ReplyDeleteChildren may struggle with arithmetic at school, but online math help services from a professional tutor can help them improve their scores. Continue reading if you want to learn more about Online Abacus Classesm and the benefits it may provide for your child. Mathgenie is an effective way to enhance grades because the courses get focused on the student's weaknesses.
ReplyDeleteSuch a very useful article. Very interesting to read this article. I would like to thank you for the efforts you had made for writing this awesome article.
ReplyDeleteสล็อตออนไลน์
Dr. Fu'S Security Blog: Malware Analysis Tutorial 9: Encoded Export Table >>>>> Download Now
ReplyDelete>>>>> Download Full
Dr. Fu'S Security Blog: Malware Analysis Tutorial 9: Encoded Export Table >>>>> Download LINK
>>>>> Download Now
Dr. Fu'S Security Blog: Malware Analysis Tutorial 9: Encoded Export Table >>>>> Download Full
>>>>> Download LINK
Glary Utilities Pro
ReplyDeleteis a powerful tool that will help you improve any type of system and performance. While it is used to get all kinds from another organized system that allows the user to choose different kinds of tools.
Glary Utilities Pro
Corel Painter 2022 Crack
Studio One 5 Crack
Infected Mushroom Manipulator Mac Crack
I guess I am the only one who came here to share my very own experience. Guess what!? I am using my laptop for almost the past 2 years, but I had no idea of solving some basic issues. I do not know how to Crack Softwares Free Download But thankfully, I recently visited a website named xxlcrack.net/
ReplyDeleteFinePrint Crack
Firebird Maestro Crack
ReplyDeleteGreate article. Keep writing such kind of info on your page.
Hello, everything is going perfectly here and ofcourse every one is sharing data,
ReplyDeletethat's truly good, keep up writing
Thanks and Best of luck to your next Blog in future.
ReplyDeleteWell this article is great. I need this article. Thanks. great share for us
ReplyDeleteI am glad to discover this page. Thank you that I had a great read!
ReplyDeleteYes i am totally agreed with this article and Excellent way of writing this issue
ReplyDeleteI was very pleased to discover this website. Nice article. Good work here
ReplyDelete
ReplyDeleteI certainly appreciate this website. D.
Stick with it! D.
ReplyDeleteStick with it! D.
ReplyDelete
ReplyDeleteINTERESTING!! you should upload more☺️ this is really good!!!D.
Everyone loves it when people come together and share opinions. D.
ReplyDeleteMicrosoft OneDrive Crack 2025 appears to be obscure stand substitute to digital webpage such Google amongst other users. Scribed are separate plans that function also to various subtitles on like a Mac and PC.
ReplyDeleteMicrosoft OneDrive Crack
Avast Internet Security Crack 2025 is a total group improved through the series to retain typically your program complete the on the internet of actual effort threats.
ReplyDeleteAvast Internet Security Crack