- Practice the use of user mode WinDbg for inspecting process in non-invasive mode
- Practice the use of IMM and WinDbg for data analysis
- Understand registry operations
- Understand file operations at multiple levels
- Understand the high level network operations
- Practice the general unpacking technique and searching for the decoding key
- Operating Systems
- Assembly Language
- Operating System Security
In this section, we go back to the analysis of lz32.dll and finish the rest of it. We will see a wide variety of malicious operations performed by the malicious lz32.dll injected by Max++, including disk formatting of the hidden drive, generation of network payload and configuration, unpacking of code segment, and infection of other system library files.
Our analysis will be mostly performed in the address range 0x3Cxxxx, and for some part we will have to dig into the raspppoe.sys again. We start the analysis from the address 0x3C1B3E. Follow the instructions below.
2. Lab Configuration
We could simply reuse the lab configuration of Tutorial 20. In general, you need two windows XP instances, one for taking notes and the other for running the malware. Also you need a WinDbg instance sitting on the host to debug the win_debug instance. Specifically, in the win_debug instance, you need to set a breakpoint at 0x3C1B3E. This is the place right before the call of loadDriver("raspppoe.sys"), as shown in Figure 1 below.
 |
| Figure 1. Code of Lz32.dll after zwLoadDriver |
3. Clean Up Operations
Recall that at 0x3C1B3F, max++ (at lz32.dll) calls zwLoadDriver to load rasppoe.sys. The behavior of rasppoe.sys is explained in the Tutorials 20 to 25. Now lz32.dll has to perform some clean up operations to further hide the trail of the malware. At 0x003C1B48 (see the first highlighted area of Figure 1), it closes the file handle of raspppoe.sys, and then from 0x3C1B55 to 0x3C1B3B, there is a loop which resumes a collection of threads one by one. This is actually to re-enable the windows file protection service.
Challenge 1. Use data tracing/breakpoint technique to prove that the loop from 0x3C1B55 to 0x3C1B3B is to re-enable the windows file protection service.
Note that major responsibility of the infected rasspppoe.sys is to set up the I/O handler for disk operations and also the infection of TDI (TCP/IP) service stack. Many services in raspppoe.sys are delayed for 15 seconds using deferred procedure call or delayed timer on system thread, because they need the further configuration done in lz32.dll. We now present the details.
4. Creation of Virtual Drive
The first interesting part of the code is the creation of a virtual drive. The code is shown in Figure 2. It consists of four steps: it first loads the "fmifs" library, and then it gets the procedure address of "FormatEx", and then it calls the function to format the drive. If you look at the stack content, you will notice the name of the drive is "C2CAD...". Once everything is done, it unloads the library.
 |
| Figure 2. Create Virtual Drive \??\C2CAD... |
5. Storing Malicious File in Hidden Drive
The next action performed by Max++ is to save the infected driver file raspppoe.sys into the newly created hidden drive. The details is shown in Figure 3.
 |
| Figure 3. Store Malicious raspppoe.sys file into Hidden Drive. file name: snifer67 |
Challenge 1. Prove that the section object used in the MapviewOfSection call at 0x3C2000 is the one for raspppoe.sys (infected driver).
Challenge 2. Find out when the snifer67 file in the hidden drive is used.
6.Configuration File
The next function to analyze is 0x3C2162. Figure 4 shows its function body. Its main job is to create the configuration file used by the TDI_SEND activities introduced in section 5 of Tutorial 25.
 |
| Figure 4. Writing IP/domain names of malicious servers |
As shown in Figure 4, Max++ loads and encodes several strings such as<ip>85.17.239.212</ip> and <host>intensivedive.com</host>. It's your job to find out all the malicious servers saved to the configuration file.
Challenge 3. Analyze the function at 0x003C20E0. What are its input parameters?
Challenge 4. Identify all the IP addresses and domain names saved into the configuration file in hidden drive.
Challenge 5. Find the name of the configuration file.
7. Saving Decoding Key in Registry
The next action Max++ performs is to save the "decoding key" which is used for self-packing into registry. Figure 5 shows the code.
 |
| Figure 5. Saving Decoding Key |
As shown in Figure 5, the decoding key is "1100100", which is retrieved from the PE header of Max+++downloader2010.exe and it is used in decoding/unpacking the code. Max++ creates a registry key in IE explorer and saves the value there.
Challenge 6. Prove that the key 11001800 is from the PE header of Max++.
Challenge 7. Find out where the key is used.
8. Creating HTTP Request
Max++ proceeds to function 3C220A, which creates the HTTP request header for downloading more malicious files. Figure 6 shows its contents. The highlighted area in Figure 6 shows the HTTP request header. It is basically to invoke /install/setup.ppc.php on intensivedive.com.
 |
| Figure 6. Creating HTTP Request Header |
9.Creation of Malicious File max++.00.x86
Next we analyze the function located at 0x3C16b8. Figure 7 shows its contents. It first opens the ntdll file and reads its basic file information. Then it creates a file called max++.00.x86 in the hidden drive. The file uses the same configuration (basic file information) of ntdll.
Challenge 8. Observe the function call at 0x3C16CD (in Figure 7). It creates a decoding table. Where does the decoding table start and end?
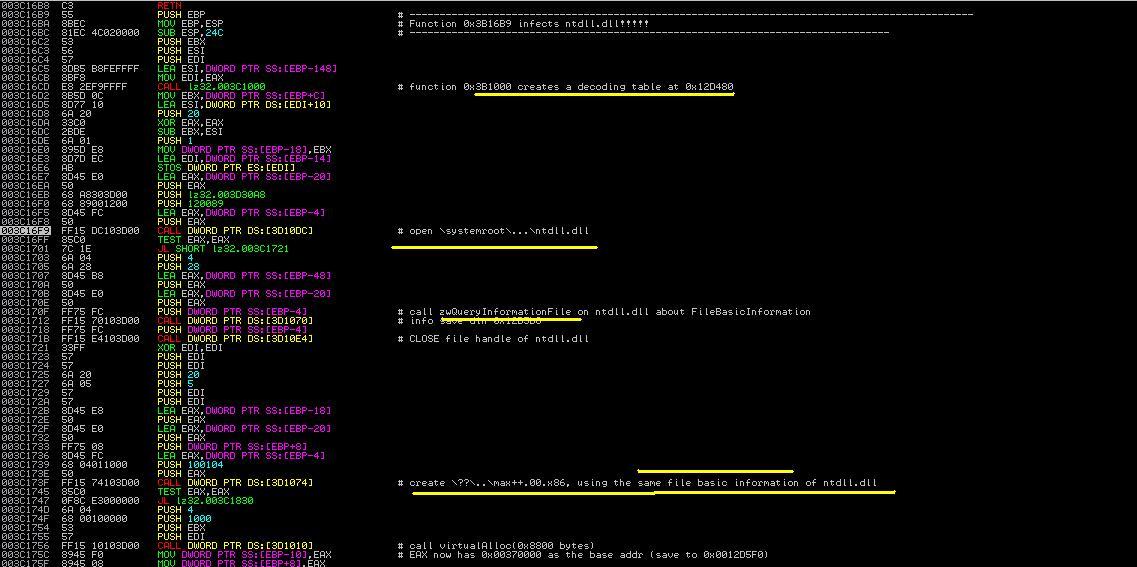 |
| Figure 7. First Part of 0x3c16b8 |
Figure 8 shows the rest of the function. It establishes the contents of max++.00.x86. The first action is to allocate a virtual memory of 0x8000 bytes (see the highlighted area in Figure 7). Then it first establishes a decoding table in the stack (in range of 0x12D3XX). Then using this decoding table, Max++ first copies the encrypted code from 0x3C2550 to 0x380000 and deciphers the information via multiple passes of decryption. Finally it writes all the contents into max++.00.x86. The file will be later loaded by another system driver.
 |
| Figure 8. Establish file max++.00.x86 |
10. Contact Malicious Server
Next Max++ contacts the malicious server, as shown in Figure 9. It constructs a winsock and connects to 85.17.239.212 and send a HTTP request to it. Notice that the interesting part is the encoding key "11001800" is embedded in the HTTP request (see the memory dump part of Figure 9). The function does not have a receive operation though. It seems to just inform the malicious server that the infection of Max++ is successful.
 |
| Figure 9. Send Traffic to intensivedive |
Being able to share the sample?
ReplyDeleteDr. Fu'S Security Blog: Malware Analysis Tutorial 26: Rootkit Configuration >>>>> Download Now
Delete>>>>> Download Full
Dr. Fu'S Security Blog: Malware Analysis Tutorial 26: Rootkit Configuration >>>>> Download LINK
>>>>> Download Now
Dr. Fu'S Security Blog: Malware Analysis Tutorial 26: Rootkit Configuration >>>>> Download Full
>>>>> Download LINK m7
informative post. Thanks for sharing.
ReplyDeleteThanks for sharing, very informative blog.
ReplyDeleteReverseEngineering
For those seeking Custom Nursing Essay Writing Service that are 100% original we have plagiarism software that the company utilizes to confirm the level of originality even when offering nursing case study writing services.
ReplyDeleteNice blog!!!!!!!.
ReplyDeleteReverseEngineering
It is very important to note that sleep performs a biological function that is fundamental to the human body, especially in teenagers more than in children and adults. So should school start later essay can debunk all misconseptions in this issues.
ReplyDeleteWanna know how to write a movie critique? In this movie critique example you can see how to do it right and what to mentions in this type of writing.
ReplyDeleteThis comment has been removed by the author.
ReplyDeletehttps://fixedcrack.com/4k-video-downloader-free-download/
ReplyDelete4K Video Downloader Patch model can be a wonderful tool for video and audio documents instantly. It stops an individual from files that are corrupted. The downloaded data files comprise high-resolution. While adequate audio excellent. Moreover, the online video Downloader has distinct languages to satisfy the wants.
https://greencracks.com/lucky-patcher-latest/
ReplyDeleteLucky Patcher APK is the best android app and patches any apps or games. it is the most popular rooted apps. it can block ads and remove unwanted system app. You Can Control easily installed apps on your Android Phone using by Patcher rooted app.
https://activatorskey.com/flixgrab-premium-crack-plus-license-key/
ReplyDeleteFlixGrab Crack is an effective program for totally installing net FLIX series. It helps to download TV shows, films, and music. The users can install all documents with quick speed. The users can install any film from net FLIX, and enjoy it offline. You can load your download list from a file, and then start to install it.
https://approvedcrack.com/clip-studio-paint-ex-crack-torrent/
ReplyDeleteClip Studio Paint EX Crack s a part of software application. It a manga studio marketed in North America. It is known as Kurisu in japan. It’s a software application for windows and macOS. It’s developed by celsius. It’s a graphics company of Japanese. Clip Studio is a software company.
https://thinkcrack.com/clip-studio-paint-torrent-crack/
ReplyDeleteClip Studio Paint Crack software is known in Japan in Kurita. macOS, Microsoft Windows, and software for iOS applications are included in it, and Celsus’s creat from the graphic software company of Japan. It is used to create a digital comic.
https://crackeypc.com/device-doctor-license-key/
ReplyDeleteDevice Doctor Crack is a useful place where you can easily find Activators, Patch, Full version software Free Download, License key, serial key, keygen, Activation Key and Torrents. Get all of these by easily just on a single click.
All matters related to medical laboratory and simple procedures People are performing a huge amount of tests daily basis on several labs world wide. but you can have all the test procedure, reporting etc here.
ReplyDeleteBlood Grouping Principle and Procedure
Hey guys! I want to thanks to all of you! Firstly to thr arthour of that wonderful blog and of course to the guys-readers of that blog! Really informative article which will be a great addition to my paper pre written to me by the group of professional writers from cheap-papers service the link to which is that one https://cheap-papers.com/buy-presentation-completed-by-experts.php so you can use their help in order to receive only the highest grades
ReplyDeleteexcellent publish, very informative. I wonder why the other specialists of this sector do not notice this.
ReplyDeleteYou must continue your writing. I’m confident, you’ve a
great readers’ base already!
Here is the Link of Free & Latest Multimedia crack:
https://softserialskey.com/cyberlink-powerdirector-ultimate-crack/
It offers a great combination of advanced functionality and great features for video editing.
It’s very simple and easy to use, so creators of every skill level can easily access its great features.
HOW TO SETUP HP ENVY 7155 TO WIFI, introduce and design simple strides to interface printers, wireless setup , driver introduce, streaming gadgets, information recuperation, email arrangement and pc rules.
ReplyDeleteGreat Article
ReplyDeleteCyber Security Projects
Networking Security Projects
JavaScript Training in Chennai
JavaScript Training in Chennai
The Angular Training covers a wide range of topics including Components, Angular Directives, Angular Services, Pipes, security fundamentals, Routing, and Angular programmability. The new Angular TRaining will lay the foundation you need to specialise in Single Page Application developer. Angular Training
Iobit keygen protected folder Keep your data and files private in the program. The only way to get this information is your password. You no longer have to worry about losing privacy.
ReplyDeleteDownload the latest Cracks with CracCOol website
ReplyDeletepatch, Serial Key, License Key and Keygen Full Free
Then again, the housing society is prepared with state of the art facilities. the facilities are simply dream of come actual for the humans of lahore. peace, protection and green behaviors. future development conserving hires and company’s with world-magnificence developers, architectures and planners. knitted ponte de roma fabrics manufacturers | knitted jacquard fabrics manufacturers
ReplyDeleteSecurity is the main aspect of computer. Different viruses and hackers attack on your computer. You discus rootkit configuration in detail. All the key points are informative. Due to some condition garage door could be broken. For this solution garage door repair Springfield provide best services.
ReplyDeleteThank you for sharing informative information. You deliver theoretical and practical work and out rootkit configuration. This post is very helpful for me. Moreover, Roofing Services Quincy MA provide the quality work at affordable price. Our expert team fulfill your desire requirements.
ReplyDeleteMy brother is amazed by this Rootkit configuration that I found for him. But really I was looking for history essay questions that I have to prepare for the next week. But it's so nice too because my brother is happy now.
ReplyDeleteTechnologistan is the popoular and most trustworthy resource for technology, telecom, business and auto news in Pakistan
ReplyDeleteIts great opportunity to get know about, What is Google My Business.
ReplyDeleteYou deliver information related to malware analysis and discuss related to rootkit configuration in detail. Thanks for sharing this post with us. Moreover, This time to take advantages of https://wilderperez.com/real-estate-agent-in-home-springs-ca/ for quality work.
ReplyDeleteYou deliver information related to malware analysis and discuss related to rootkit configuration in detail. Thanks for sharing this post with us. Moreover, This time to take advantages of real estate agent in home springs ca for quality work.
ReplyDeleteEnjoyed reading the article above, Really explains everything in detail, the article is very interesting and effective. Thank you and good luck for the upcoming articles...For more please visit: SEO Service USA...
ReplyDeleteYou deliver the informative information related to security and algorithms in detail. This post is very helpful for IT students. Further, This time to take advantages of car locksmiths in san Antonio tx for quality work.
ReplyDeleteVery Informative & watchful content, You guys also try it
ReplyDeleteReal Estate Agents Meridian ID
for best Relocation services
Very nice article and straight to the point. I don’t know if this is truly the best place to ask but do you folks have any idea where to get some professional writers? Thank you. 호텔카지노
ReplyDeleteI finally found what I was looking for! I'm so happy. 우리카지노
ReplyDeleteI really happy found this website eventually. Really informative and inoperative, Thanks for the post and effort! Please keep sharing more such blog. 한국야동
ReplyDeletePlease visit once. I leave my blog address below
야설
일본야동
Thanks for taking the time to discuss this, I feel strongly about it and love learning more on this topic. If possible, as you gain expertise, would you mind updating your blog with extra information? It is extremely helpful for me. 야동
ReplyDeletePlease visit once. I leave my blog address below
국산야동
일본야동
Excellent read, I just passed this onto a friend who was doing some research on that. I will learn a lot of new stuff right here! 국산야동
ReplyDeletePlease visit once. I leave my blog address below
한국야동
국산야동
Great article with excellent idea!Thank you for such a valuable article. I really appreciate for this great information. 한국야동
ReplyDeletePlease visit once. I leave my blog address below
야동
일본야동
Excellent article. Very interesting to read. I really love to read such a nice article. Thanks! keep rocking.
ReplyDeleteIDM Crack
Ezdrummer Crack
Windows 10 Activatior Crack
REFX Nexus VST Crack
Virtual Serial Ports Crack
Kerio Control Crack
Attractive component of content. I just stumbled upon your site and in accession capital to claim that I acquire actually enjoyed account your blog posts. Anyway I will be subscribing for your feeds or even I success you access consistently quickly.
ReplyDelete섯다
I am sure this post has touched all the internet users, its really really pleasant piece of writing on building up new webpage.
ReplyDelete토토
I am really glad to glance at this website posts which includes plenty of
ReplyDeleteuseful data, thanks for providing such information.
일본야동
great & nice articles with a lot of information to read...great people keep posting and keep updating people..thank you , Hello, this is very useful material.
ReplyDelete스포츠토토존
Great Post. Keep Writing and Inspiring. Looking Forward to More.
ReplyDeleteThank you for sharing such a Wonderful Blog.
ReplyDeleteI really enjoy your Post. Very creative and Wonderful.
ReplyDeleteDr. Fu'S Security Blog: Malware Analysis Tutorial 26: Rootkit Configuration >>>>> Download Now
ReplyDelete>>>>> Download Full
Dr. Fu'S Security Blog: Malware Analysis Tutorial 26: Rootkit Configuration >>>>> Download LINK
>>>>> Download Now
Dr. Fu'S Security Blog: Malware Analysis Tutorial 26: Rootkit Configuration >>>>> Download Full
>>>>> Download LINK
Great post, beautiful weblog with great informational content. This is a really interesting and informative content. 토토사이트
ReplyDeleteGreat Post. Looking Forward to more.
ReplyDeleteGreat blog. Looking forward to More.
ReplyDeletebetflix The game has a style that is easy to play, สล็อตpg
ReplyDeleteFor quite some time Gorilla INC. has been a tenable piece of the Trenton NJ people group to assist clients with their different requirements.
ReplyDeletewater filtration trenton nj
All-State Roofing and Siding's Roofing Contractors Bayonne NJ is an excellent choice on which you could rely. We provide superior, unmatched, and genuine services.
ReplyDeleteroofing contractors bayonne nj
Wish you all the best for your new upcoming articles and kindly write on topic Ecommerce website and also on Cheap web design thanks.
ReplyDeleteThanks for sharing your blogs are good and informative keep sharing such good content.
ReplyDeleteInvestment in real estate
تركيب طارد الحمام
ReplyDeleteشركة تركيب طارد الحمام
slot siteleri
ReplyDeletekralbet
betpark
tipobet
betmatik
kibris bahis siteleri
poker siteleri
bonus veren siteler
mobil ödeme bahis
8QA
The policy of mechanisms in buy college research paper shows the development of the system and increases flexibility to modern requirements. They operate with free methods of building blocks of available information for the implementation of this mechanism.
ReplyDeletejewellery online Jewellery design is an art form that involves creating unique and beautiful pieces of jewellery, such as necklaces, bracelets, earrings, and rings. It is a process that requires creativity, skill, and attention to detail. A jewellery designer must be knowledgeable about different materials, such as precious and semi-precious stones, metals, and beads, and be able to incorporate these materials into their designs to create a beautiful and cohesive piece.
ReplyDeleteThe jewellery design process begins with an idea or inspiration. The designer may draw sketches or create digital designs to visualize their ideas. From there, they will select the materials they want to use and start creating the piece. Depending on the design, the process may involve using traditional techniques, such as soldering and casting, or newer technologies like 3D printing.
A skilled jewellery designer must pay close attention to the details of the piece, such as the size, shape, and arrangement of stones or beads, as well as the overall aesthetic. They must also consider the wearability and comfort of the jewellery piece, ensuring that it is both beautiful and functional.
Jewellery design is a constantly evolving field, with new trends and styles emerging all the time. From minimalist and understated designs to bold and statement-making pieces, there is a wide range of jewellery styles to choose from. With the right combination of creativity and technical skill, a jewellery designer can create beautiful and unique pieces that can be treasured for a lifetime jewellery design
Your blog is a treasure trove of useful information for homeowners. The segment about Roof installation company near you caught my eye, as it's a crucial aspect of home maintenance. Your recommendations and advice are truly appreciated.
ReplyDelete
ReplyDeleteI hope to see more post from you.
إذا كنت تبحث عن أفضل شركة صيانة أفران بالرياض يمكنك اللجوء إلى شركة كلينر للتنظيف التي تمتلك خبرة واسعة في هذا المجال، كما يوجد لديها فريق فني مدرب على مستوى عالي للقيام بأعمال صيانة الأفران بجميع أنواعها، هذا بالإضافة إلى فريق عمل آخر يقوم بتنظيف الأفران.
ReplyDeleteشركة كلينر لصيانة الافران والتنظيف بالرياض
هل تبحث عن مؤسسة لحل مشكلة انسداد الصرف الصحي وتسليك المجاري؟ شركة صقور الجزيرة هي الخيار الامثل لحل مشكلتك نهائيا.
ReplyDeleteعلاج انسداد المجاري
شركة النور لتوفير خدمة تسليك المجاري بالدمام بأفضل التقنيات وامهر العمال.
ReplyDeleteشركة تسليك مجاري بالضغط بالدمام
ماستر كلين لخدمات التنظيف تقدم خدمات شاملة بمدينة تبوك بأفضل الاسعار
ReplyDeleteافضل شركة تنظيف بتبوك
شركة كلين الرياض من اكبر شركات التنظيف بالمملكة حيث توفر افضل الاسعار والادوات والعمال، مع شركة كلين الرياض منزلك في ايدٍ امينة.
ReplyDeleteشركة تنظيف بالرياض
ان تنظيف الخزانات وتعقيمها من الاساسيات للحفاظ على نقاء المياه ومنع تلوثها ، شركة حور كلين تفعل ذلك عنك بأحسن طريقة وارخص سعر.
ReplyDeleteشركة تنظيف خزانات بالرياض
Looking forward to reading more. Great article post. Fantastic. Thanks so much for the blog
ReplyDeleteIts a great pleasure read this post. Awesome! Its full of information here
ReplyDeleteI have you bookmarked to check out new stuff post. keep it up. Its greatt
ReplyDeleteIts hard to find good ones. I have added this blog to my favorites. Thank You
ReplyDelete
ReplyDeleteI don't suppose I've read something like that before. D.
So nice to find someone with a few original thoughts on this subject matter. D. 🙂
ReplyDeleteIt is in reality a great and useful piece of info. D.
ReplyDelete
ReplyDeleteThanks for sharing. 🙂 D.
Perfectly composed articles , thankyou for information. 🙂 D.
ReplyDeleteLike!! Really appreciate you sharing this blog post.D.
ReplyDeleteغسيل مكيفات بالاحساء 4vdRQa1c3I
ReplyDeleteشركة تنظيف مجالس بحفر الباطن
ReplyDelete15 fgqikJvreL
شركة نظافة بالقطيف
ReplyDeleteFj2pqwbId12
عزل فوم المجمعة
ReplyDeletebdgXWmDW9
عزل فوم المجمعة
ReplyDeletek0xiTQkLhZ
Unity Pro Crack these days is the mainly trending application for rising elevated-excellence sports event down by the compatibility to put in 3D consistency. To hold up developers in this stare, this software authorizes you to introduce 3D material as of outside depiction agenda similar to Maya, 3ds Max, mixer, as well as greatly extra.
ReplyDeleteUnity Pro Crack
احسنت تابع معنا خدمات الغسيل وتقنية البخار كوسيلة فعالة لتنظيف السجاد والمجالس تتميز شركة تنظيف منازل بالاحساء هذه الطريقة بقدرتها على التخلص من الأوساخ والجراثيم دون الحاجة إلى المواد الكيميائية الضارة
ReplyDeleteشركة تنظيف بالهفوف
خدمة ممتازة مع
ReplyDeleteشركة تسليك مجاري في الشارقة
الفريق عنده خبرة كبيرة واشتغلوا بسرعة وبدقة، وبعد التسليك المشكلة اتحلت تمامًا والمجاري بقت شغالة بشكل طبيعي.
شكرا علي الخدمة نتمنا المزيد تابعنا في شركة ولاد البلد تجد خدمة تنظيف رائحة البيت المتغيرة باستمرار بدون جهدًا وتركيزًا على مصادر الروائح مع تطبيق النصائح المذكورة من شفط صرف صحى عجمان سيكون بالإمكان الحفاظ على جو نظيف وذو رائحة مع الوقاية من الروائح الكريهة تبدأ من المعرفة والالتزام بأنظمة النظافة والرعاية الصحيحة لبيئة المعيشة تابع شركة تسليك مجاري بالشارقة وستفيد من خدماتنا المجانية .
ReplyDeleteاهتم براحة منزلك بجودة الخدمات التي تستحقها.
ReplyDeleteشركة تنظيف مكيفات في الشارقة تقدّم تنظيفًا متكاملًا يشمل الفلاتر، المراوح، والملفات الداخلية للمكيف.
الفريق متخصص ويستخدم معدات حديثة لضمان أداء رائع.
اختيارك يستحق الأفضل لجهازك ولسلامة الهواء داخل المنزل.